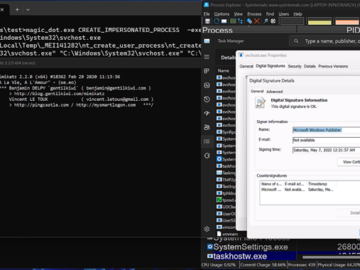
CrushFTP is a file transfer server that supports secure protocols, offers easier configuration, and offers powerful monitoring tools. It also…
Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by…
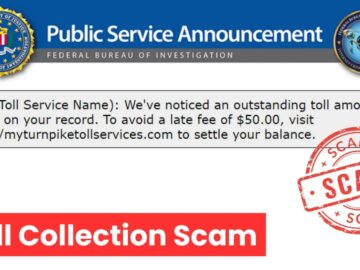
The FBI’s Internet Crime Complaint Center (IC3) has warned about a sophisticated smishing scam targeting drivers across multiple states. Since…
Cybersecurity experts from SafeBreach have revealed a series of vulnerabilities that could allow attackers to remotely delete files on a…
April 18, 2024 – A major international law enforcement effort has disrupted the notorious LabHost phishing-as-a-service platform. April 18, 2024…
Hackers are now offering administrative access to over 3000 Fortinet SSL-VPN devices. This breach poses a significant threat to the…
With the tightening grip of Chinese regulatory measures on foreign digital services, Apple Inc. has removed several major messaging apps,…
Citrix’s uberAgent, a sophisticated monitoring tool used to enhance performance and security across Citrix platforms, has been identified as having…
European Union Aviation Safety Agency (EASA) has issued a cautionary alert following reports of cyber-attacks targeting flights bound for the…
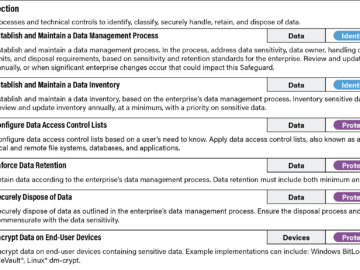
In this article, we’ll identify some first steps you can take to establish your cloud security strategy. We’ll do so…
Apr 22, 2024NewsroomCryptocurrency / Artificial Intelligence Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial…
A flaw in the Forminator plugin impacts hundreds of thousands of WordPress sites Pierluigi Paganini April 22, 2024 Japan’s CERT…