Akira ransomware received $42M in ransom payments from over 250 victims Pierluigi Paganini April 21, 2024 Government agencies revealed that…
You rarely root for a cybercriminal, but a new malware campaign targeting child exploiters doesn’t make you feel bad for…
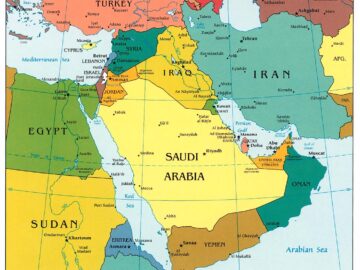
DuneQuixote campaign targets the Middle East with a complex backdoor Pierluigi Paganini April 21, 2024 Threat actors target government entities…
Ransomware actors have had a rough start this year, as stats from cybersecurity firm Coveware show companies are increasingly refusing…
Security Affairs newsletter Round 468 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini April 21, 2024 A new round of…
By Mike Starr, CEO of Trackd It’s often paid lip service to (or worse, intentionally neglected), and rarely appreciated, but…
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised…
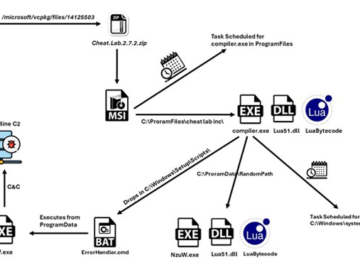
A new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal….
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Palo Alto firewalls: Public exploits,…
Critical CrushFTP zero-day exploited in attacks in the wild Pierluigi Paganini April 20, 2024 Threat actors exploited a critical zero-day…
The Forminator WordPress plugin used in over 500,000 sites is vulnerable to a flaw that allows malicious actors to perform unrestricted…
A French hospital was forced to reschedule procedures after cyberattack Pierluigi Paganini April 20, 2024 A French hospital was forced…