Apr 12, 2024The Hacker NewsDevSecOps / Identity Management Identities now transcend human boundaries. Within each line of code and every…
Wiz, a leading cloud security company, has announced its acquisition of Gem Security for $350 million. This acquisition marks a…
DuckDuckGo has launched Privacy Pro, a new subscription service that promises to enhance user privacy across the web. This innovative…
Apr 12, 2024NewsroomNetwork Security / Zero-Day Palo Alto Networks is warning that a critical flaw impacting its PAN-OS software used…
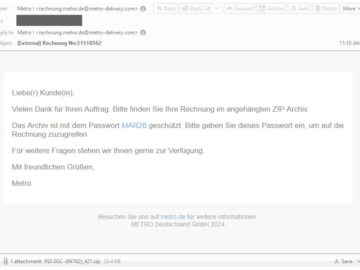
TA547 targets German organizations with Rhadamanthys malware Pierluigi Paganini April 12, 2024 TA547 group is targeting dozens of German organizations with…
Factoring in whether to allocate resources for a bug bounty program in your annual cybersecurity budget can be a challenging…
Bitdefender GravityZone Update Server (versions 6.36.1, Endpoint Security for Linux 7.0.5.200089, and Endpoint Security for Windows 7.9.9.380) is vulnerable to…
In response to a recent data breach at Sisense, a provider of data analytics services, the U.S. Cybersecurity and Infrastructure…
The Iranian threat actor known as MuddyWater has been attributed to a new command-and-control (C2) infrastructure called DarkBeatC2, becoming the…
Ukrainian hackers have successfully infiltrated and disabled a vast network of industrial sensors and monitoring infrastructure in Russia, leading to…
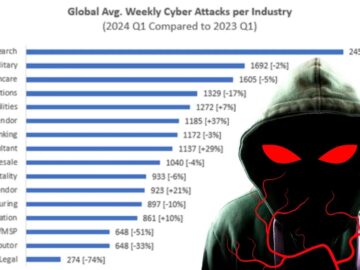
In Q1 2024, Check Point Research (CPR) witnessed a notable increase in the average number of cyber attacks per organization…
Zscaler has announced the acquisition of Airgap Networks, a company renowned for its agentless segmentation technology. This acquisition is set…