The Matanbuchus malware has been reported to initiate a new campaign, exploiting XLS files to compromise Windows machines. This sophisticated…
March 8, 2024 – The flaws could allow an attacker with privileged access to a guest VM to access the…
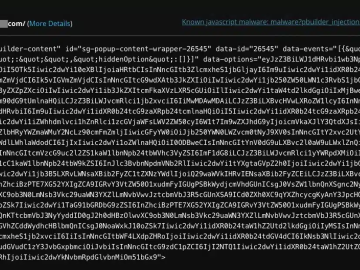
Hackers exploited WordPress Popup Builder plugin flaw to compromise 3,300 sites Pierluigi Paganini March 11, 2024 Threat actors are hacking…
NSA and CISA jointly released “Top 10 Cloud Security Mitigation Strategies” to advise cloud users on critical security practices for…
Beware of phishing and malspam scams targeting your Software-as-a-Service (SaaS) logins! Cybercriminals are using fake Dropbox emails to steal login…
With hybrid cloud no longer merely a stop along the way to full-fledged public cloud, tackling management complexity is essential….
The Lindsay Municipal Hospital cyberattack has been claimed by the BianLian ransomware group. This nefarious organization, known for its disruptive…
VMware’s ESXi, Workstation, and Fusion products could allow attackers to execute malicious code on affected systems. Impacted VMware Products These…
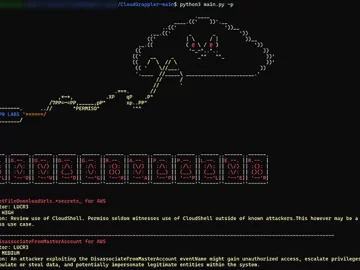
CloudGrappler is an open-source tool designed to assist security teams in identifying threat actors within their AWS and Azure environments….
Mar 11, 2024NewsroomZero-Day / Endpoint Security A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities…
Each method is weaponized—almost always against women—to degrade, harass, or cause shame, among other harms. Julie Inman Grant, Australia’s e-safety…
This collection of free cybersecurity guides covers a broad range of topics, from resources for developing cybersecurity programs to specific…