Refuah Health Center has committed to investing $1.2 million in enhancing its cybersecurity measures and will also pay $450,000 in…
Hackers use Remote Access Trojans (RATs) to gain unauthorized access and control over a victim’s computer remotely. These malicious tools…
Cacti, the performance and fault management framework, has been discovered with a blind SQL injection vulnerability, which could reveal Cacti…
A blind SQL injection vulnerability (CVE-2023-51448) in Cacti, a widely-used network monitoring, performance and fault management framework, could lead to…
Jan 09, 2024The Hacker NewsSaaS Security / Data Security Collaboration is a powerful selling point for SaaS applications. Microsoft, Github,…
Australian travel agency Inspiring Vacations has fallen victim to a data breach, exposing passport and travel details of thousands of…
QNAP has released multiple security advisories for addressing several high, medium, and low-severity vulnerabilities in multiple products, including QTS, QuTS…
In an era where information is as valuable as currency, intellectual property (IP) theft has emerged as a silent yet formidable threat…
Jan 09, 2024NewsroomNetwork Security / Data Protection A security flaw has been disclosed in Kyocera’s Device Manager product that could…
A dark web user has allegedly claimed the African Bank data breach and is purportedly selling sensitive data on the…
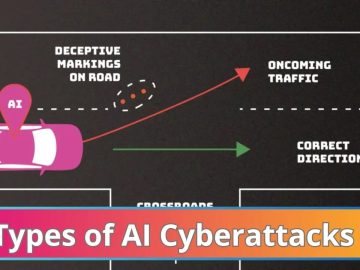
Artificial intelligence (AI) systems can be purposefully tricked or even “poisoned” by attackers, leading to severe malfunctions and striking failures….
Brijesh Singh, a distinguished Indian Police officer from the 1996 batch of IPS (Indian Police Service), has etched his name…