In today’s almost entirely digitised, cyber world, it’s imperative that private data and passwords remain secure and protected at all…
Saudi Ministry exposed sensitive data for 15 months Pierluigi Paganini January 08, 2024 Saudi Ministry of Industry and Mineral Resources…
The LockBit ransomware operation has claimed responsibility for a November 2023 cyberattack on the Capital Health hospital network and threatens…
Accessing an online account typically requires a username and password, but cybersecurity researchers at CloudSEK have uncovered a disturbing trend…
In a landmark victory for cybersecurity, the xDedic Marketplace, a notorious haven for cybercrime, has been shut down. This international…
Jan 08, 2024NewsroomMalware / Cybercrime Threat actors operating under the name Anonymous Arabic have released a remote access trojan (RAT)…
Russian hackers have been inside Ukrainian telecoms company Kyivstar’s system since at least May of last year, causing the most…
AsyncRAT is an open-source remote access Trojan (RAT) malware known for its ability to provide unauthorized access and control over…
The cost of rebuilding the British Library’s systems following the October Rhysida ransomware attack is likely to hit between £6m…
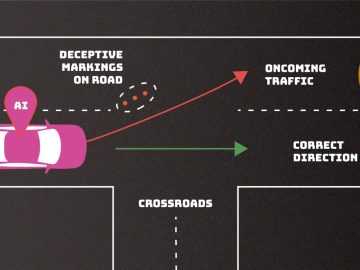
The National Institute of Standards and Technology (NIST) has exposed critical AI vulnerabilities, creating potential avenues for malicious actors to…
With the general public now alert to and furious over the mistreatment of subpostmasters, the government must take the opportunity…
DoJ charged 19 individuals in a transnational cybercrime investigation xDedic Marketplace Pierluigi Paganini January 08, 2024 19 individuals worldwide were…