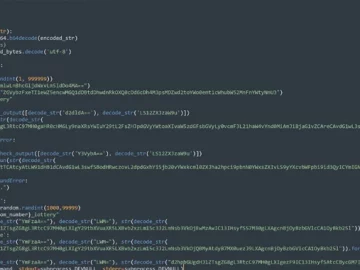
Jan 04, 2024NewsroomCryptocurrency Miner / Malware Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source…
The Spanish unit of telecoms provider Orange, the telecommunications behemoth, encountered disruptions in its internet services due to cyberattack. Users…
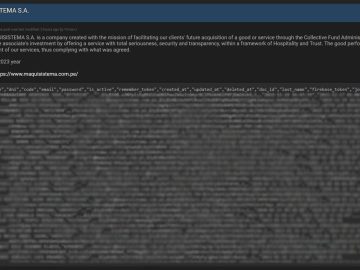
Peru-based financial organization Maquisistema has been allegedly impacted by a data breach. A threat actor going by the alias “God…
Previously, in December 2023, it was reported that SSH servers were vulnerable to the new Terrapin Attack in which threat…
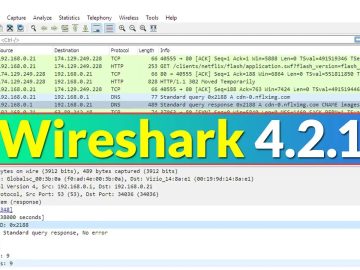
A free and open-source packet analyzer, Wireshark is used for network troubleshooting, education, software and communications protocol development, and analysis. …
In recent months, a staggering 29 malware families have been discovered targeting approximately 1800 banking applications worldwide. This revelation, based…
Malicious stockpiled domains are the collection of domain names that threat actors acquire in advance for several types of future…
Active Directory infiltration methods exploit vulnerabilities or weaknesses in Microsoft’s Active Directory to gain unauthorized access. Active Directory is a…
Over the holidays, the npm package registry was flooded with more than 3,000 packages, including one called “everything,” and others named a…
On Wednesday, the London Public Library stated that certain workers’ personal information was stolen by the hackers responsible for the…
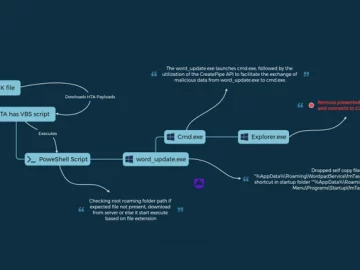
Jan 04, 2024NewsroomSoftware Security / Malware The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT…
Wireshark is a popular open-source network protocol analyzer that allows users to inspect and capture data on a network in…