The University of Lincoln has shared details of the work it has done to ensure the uptime and resiliency of…
WooliesX’s managing director Amanda Bardwell is set to become CEO of Woolworths Group in September, as current chief Brad Banducci…
ConnectWise fixed critical flaws in ScreenConnect remote access tool Pierluigi Paganini February 20, 2024 ConnectWise addressed two critical vulnerabilities in…
A team of academic researchers show that a new set of attacks called ‘VoltSchemer’ can inject voice commands to manipulate a smartphone’s…
In a significant development in the fight against cybercrime, Ukrainian national Mark Sokolovsky, 28, has been extradited to the United…
[By Brett Walkenhorst, Ph.D., CTO, Bastille] Zero Trust has been an important paradigm for advancing network security for almost 15…
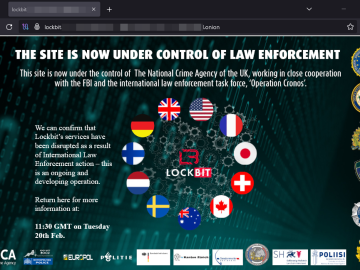
In an act of exquisite trolling, the UK’s National Crime Agency (NCA) has announced further details about its disruption of…
The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world’s most important guidelines for…
News that the prolific, dangerous and feared LockBit ransomware cartel has been significantly disrupted by the UK’s National Crime Agency…
Melbourne-headquartered email hosting provider Fastmail has said that the eSafety Commissioner’s proposed industry standards, requiring message and online file-storage providers…
VMware urged admins today to remove a discontinued authentication plugin exposed to authentication relay and session hijack attacks in Windows domain…
A critical Remote Code Execution (RCE) vulnerability in the Bricks Builder theme for WordPress has put over 25,000 websites at…