Ahead of the ninth edition of the Future Investment Initiative in Riyadh, Saudi Arabia, Humain and Qualcomm Technologies announced a…
As Cybersecurity Awareness Month continues, we wanted to dive even deeper into the attack methods affecting APIs. We’ve already reviewed…
The Beast ransomware group has emerged as a significant threat in the cybersecurity landscape, evolving from the Monster ransomware strain…
Tata Motors, India’s largest automaker and a major player in the global automotive industry, suffered a catastrophic data exposure that…
Saudi Arabia’s push to transform its healthcare system has taken a bold technological leap. The Ministry of Health (MoH), in…
CISA has added two critical vulnerabilities affecting Dassault Systèmes DELMIA Apriso to its Known Exploited Vulnerabilities catalog, warning that threat…
A path traversal vulnerability discovered in Docker Compose allows attackers to write arbitrary files to host systems through specially crafted…
Oct 29, 2025Ravie LakshmananMalware / Threat Intelligence Cybersecurity researchers have discovered a set of 10 malicious npm packages that are…
A threat actor has claimed responsibility for breaching HSBC USA, alleging possession of a vast database containing sensitive customer personal…
A sophisticated supply chain attack involving ten malicious npm packages that execute automatically upon installation and deploy a comprehensive credential…
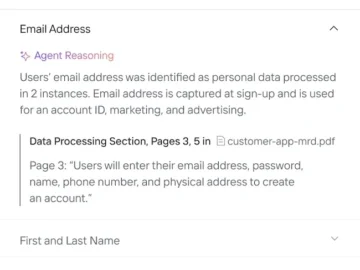
Privado.ai released several new capabilities to automate privacy assessments and data maps for privacy teams amid growing privacy enforcement for…
U.S. CISA adds Dassault Systèmes DELMIA Apriso flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini October 29, 2025 U.S….