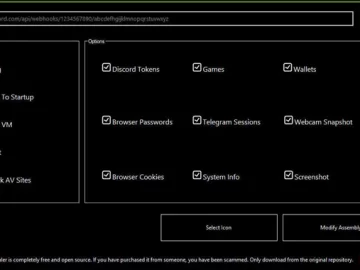
Oct 17, 2023NewsroomMalware / APT In what’s the latest evolution of threat actors abusing legitimate infrastructure for nefarious ends, new…
Prove Identity, a late-stage startup with roots in the ecommerce mobile payments space, on Tuesday closed a $40 million funding…
The Android ‘SpyNote’ malware was observed in attacks targeting Italy using a fake ‘IT-alert’ public alert service that infected visitors…
In today’s business landscape, information security is of paramount importance. With nearly all business operations going digital, companies are increasingly…
New research by Outpost24 has revealed that IT administrators could be just as predictable as end-users when it comes to…
Hacktivists have launched hundreds web defacement attacks against targets in Israel following the devastating attack by Hamas on Israeli civilians…
Today, Cato Networks announced the findings of its 2023 SASE Adoption Survey. The survey of 1,694 IT leaders worldwide finds that management…
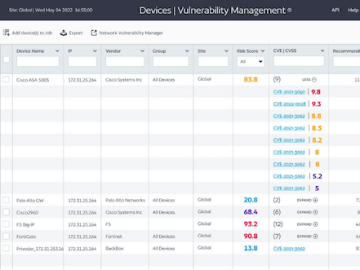
BackBox launched Network Vulnerability Manager (NVM). With this new capability added to its existing Network Automation Platform, BackBox integrates automated…
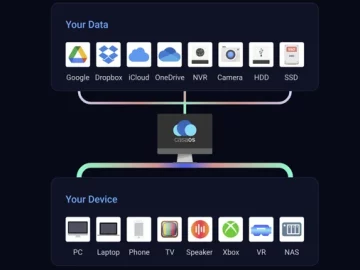
Oct 17, 2023NewsroomVulnerability / Cyber Threat Two critical security flaws discovered in the open-source CasaOS personal cloud software could be…
Medical and janitorial equipment supplier Countrywide Healthcare has deployed a service assurance management platform from Highlight to manage the Cisco…
San Diego-based MemComputing is researching the use of in-memory processing ASICs (Application Specific Integrated Circuits) to potentially crack 2048 bit…
As an IT professional, you know that threat actors work overtime to get your end-users’ credentials. Whether it’s 3 PM…