In the wake of the Israel-Gaza conflict, threat actors have been observed targeting Israeli rocket alerting applications to spread fear…
Hacker group CyberAv3ngers has claimed responsibility for a major cyberattack on ORPAK Systems, a prominent provider of gas station solutions…
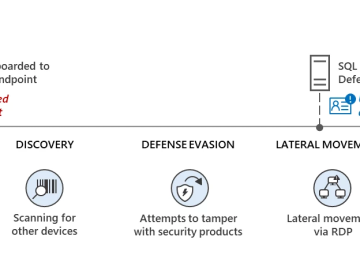
Microsoft Defender thwarted Akira ransomware attack on an industrial engineering firm Pierluigi Paganini October 16, 2023 Microsoft thwarted a large-scale…
Modern-day attack surface management (ASM) can be an intimidating task for most organizations, with assets constantly changing due to new…
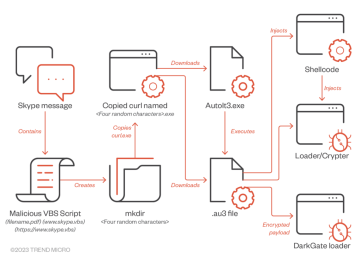
DarkGate campaign abuses Skype and Teams Pierluigi Paganini October 16, 2023 Researchers uncovered an ongoing campaign abusing popular messaging platforms…
If only fast IT operations (ITOps) was just about choosing the right tooling. Instead, as so often in IT, ensuring…
A massive healthcare database linked to Palestine has been compromised by a threat actor, resulting in the exposure of more…
ALPHV ransomware group named the internationally known ITM and ATM solutions provider QSI Inc. as its victim. Quality Service Installation…
Hackers utilized the Teams and Skype messaging platforms to spread the DarkGate malware to the targeted businesses. When DarkGate malware…
Cybercriminals behind the AvosLocker ransomware attack employed a tactic of infecting organizations through Open-Source Remote Administration Tools. This method allowed…
LockBit Ransomware Demands $80 Million from CDW Technology Giant Sirius Federal servers of the CDW technology service provider have fallen…
Signal messenger has investigated rumors spreading online over the weekend of a zero-day security vulnerability related to the ‘Generate Link…