A flaw in libcue library impacts GNOME Linux systems Pierluigi Paganini October 10, 2023 A vulnerability in the libcue library…
Tag CVE ID CVE Title Severity Active Directory Domain Services CVE-2023-36722 Active Directory Domain Services Information Disclosure Vulnerability Important Azure…
Last week on Malwarebytes Labs: Multi-factor authentication has proven it works, so what are we waiting for? Amazon Prime email…
Microsoft’s security response team on Tuesday pushed out a massive batch of software and OS updates to cover more than…
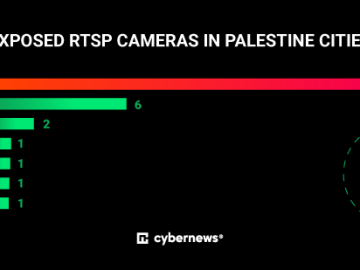
Exposed security cameras in Israel and Palestine pose significant risks Pierluigi Paganini October 10, 2023 Many poorly configured security cameras…
Microsoft has released the Windows 11 22H2 KB5031354 cumulative update to fix security vulnerabilities. This is the first Patch Tuesday update…
Spanish airline Air Europa, the country’s third-largest airline and a member of the SkyTeam alliance, warned customers on Monday to…
A few tips and how-tos for when you are ready to move to the next Android phone. Backup, transfer, wipe,…
Microsoft is planning to phase out VBScript in future Windows releases after 30 years of use, making it an on-demand…
This week on the Lock and Code podcast, we speak with Bay Area teenager Nitya Sharma—for the second year in…
Software maker Adobe on Tuesday released fixes for at least 13 security vulnerabilities in multiple product lines, warning that critical…
Microsoft is planning to phase out VBScript in future Windows releases after 30 years of use, making it an on-demand…