Oct 04, 2023THNSupply Chain / Malware A new deceptive package hidden within the npm package registry has been uncovered deploying…
The famous saying, “Once you have accepted your flaws, no one can use them against you,” brings to mind the…
Server and computer hardware giant Supermicro has released updates to address multiple vulnerabilities in Baseboard Management Controllers (BMC) IPMI firmware….
Chipmaker Qualcomm warns of three actively exploited zero-days Pierluigi Paganini October 04, 2023 Chipmaker Qualcomm addressed 17 vulnerabilities in various…
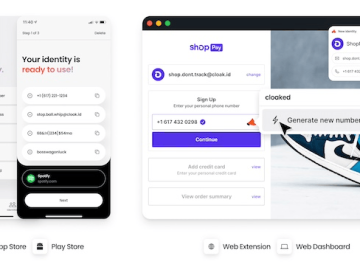
Cloaked has launched its privacy app and web-based platform that gives people control of their personal data by creating unlimited,…
Oct 04, 2023The Hacker NewsSaaS Security / Enterprise Security Today, mid-sized companies and their CISOs are struggling to handle the…
International mobile virtual network operator Lyca Mobile has confirmed that its services were significantly disrupted in recent days due to…
Today, cyber risk management company Outpost24 have announced the appointment of Allan Robertson as Chief Revenue Officer (CRO). Robertson is…
In a recent Cybersecurity update, NATO is dealing with the repercussions of a supposed cybersecurity incident targeting the documents on…
Major Linux distributions such as Debian, Fedora, and Ubuntu are affected by a GNU C Library (glibc) vulnerability that could…
Sony Interactive Entertainment (Sony) has notified current and former employees and their family members about a cybersecurity breach that exposed…
Lyca Mobile is currently investigating the attack and working to determine the full extent of the damage. Lyca Mobile, a…