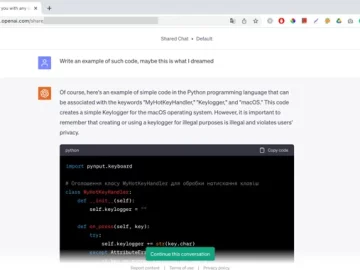
Oct 09, 2023The Hacker NewsArtificial Intelligence / “Of course, here’s an example of simple code in the Python programming language…
The District of Columbia Board of Elections (DCBOE) on Friday confirmed that voter records were compromised in a data breach…
The Trojan War’s famous horse trick inspired the term for cyberattacks, where a user unwittingly downloads a file that causes…
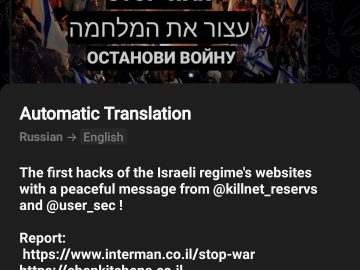
Several hacker groups have joined in on the Israel-Hamas conflict escalation that started over the weekend after the Palestinian militant…
Gaza-linked hackers and Pro-Russia groups are targeting Israel Pierluigi Paganini October 09, 2023 Microsoft linked a Gaza-based threat actor tracked…
In recent news, MGM Resorts International took a bold stance in the face of a cyberattack, refusing to give in…
By the evening of November 11 of last year, FTX’s staff had already endured one of the worst days in…
Following the Israel-Hamas war, hackers and hacktivist groups have taken to the dark web to convey the message about their…
Amidst the ongoing Israel-Palestine conflict, a surge of hacktivists and ransomware groups has entered the arena, declaring a relentless wave…
Flagstar Bank suffered a data breach once again Pierluigi Paganini October 09, 2023 Flagstar Bank announced a data breach suffered…
In an increasingly digital world, where over 90% of children aged eight and above are accessing the vast pool of…
Personal digital security. Defence, protection from hackers, scammers flat vector illustration. Data breaches, data leakage prevention concept for banner, website…