A new supply chain attack has compromised multiple npm packages maintained by the crowdstrike-publisher account, marking a worrying continuation of…
Around 40 years ago, a bank branch manager probably knew the name of every customer and was able to offer…
Jaguar Land Rover said Tuesday that it will extend a production pause until Sept. 24, as it continues investigating a…
Microsoft has announced that the Windows Management Instrumentation Command-line (WMIC) tool will be removed after upgrading to Windows 11 25H2 and later….
Las Vegas, United States, September 16th, 2025, CyberNewsWire Seraphic today announced at Fal.Con 2025 that its Secure Enterprise Browser (SEB)…
LastPass Evolves Secure Access Experiences to Combat Shadow IT and AI Risks for CISOs Picture your organization humming along, with…
When you are done with the burner phone, make sure that you get rid of it in a thoughtful way…
Seraphic today announced at Fal.Con 2025 that its Secure Enterprise Browser (SEB) solution is now available for purchase in the…
Clients should have clear expectations of a cloud SLA, and if a provider falls short, they must be held accountable….
The web browser has quietly become one of the most critical components of enterprise infrastructure—and one of the most dangerous….
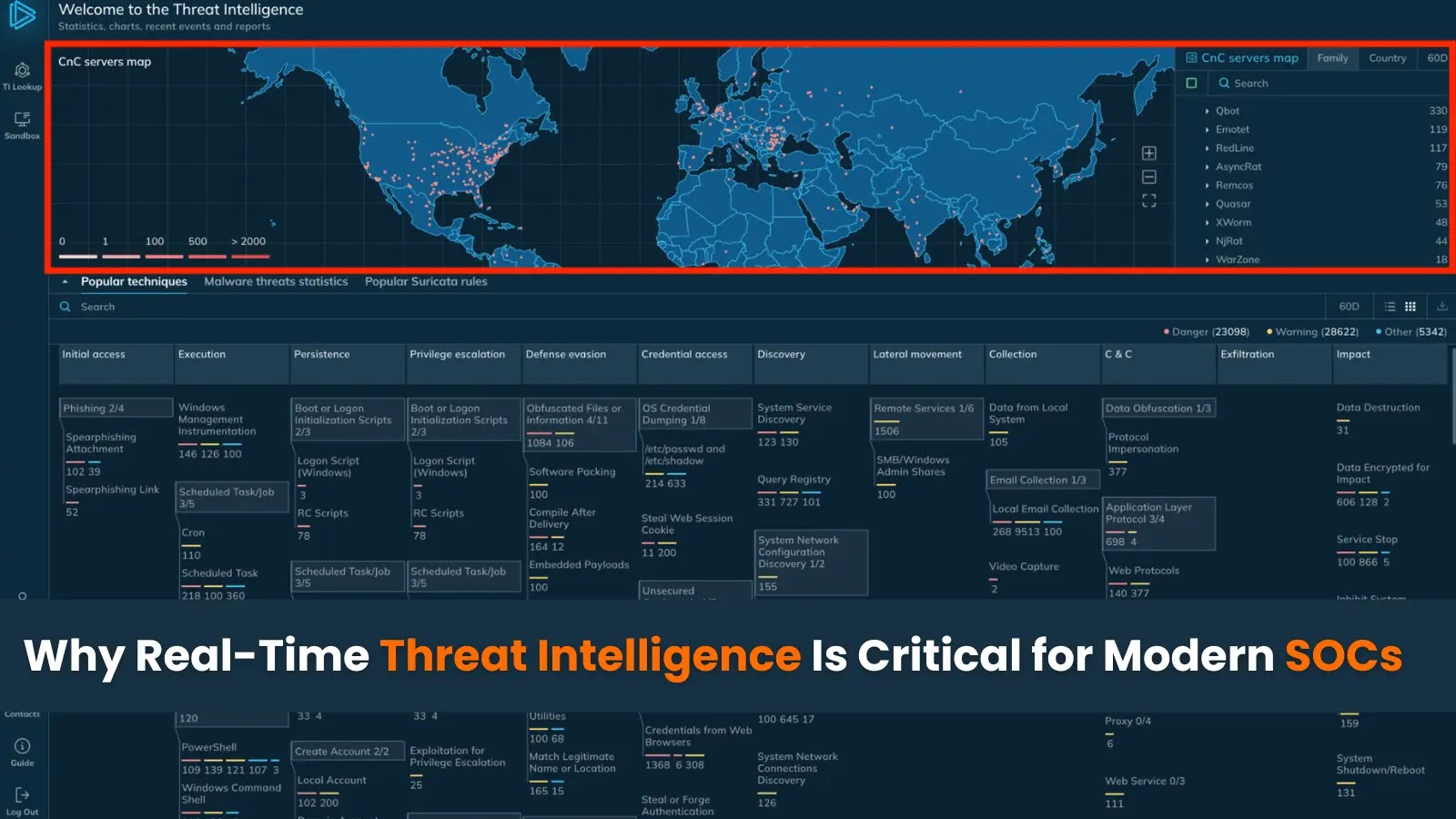
Security Operations Centers (SOCs) exist under ever-increasing pressure to detect and respond to threats before they escalate. Today’s fast-moving adversaries…
Sekoia.io’s Threat Detection and Response (TDR) team has uncovered a sophisticated campaign by APT28 that weaponizes Signal Messenger to deploy…