Regulatory compliance and cybersecurity improvement are not two sides of the same coin: they are distinct pillars that demand specialized…
As AI technology advances, it is essential to remain mindful of familiar and emerging risks. Education is critical to fostering…
An overwhelming number of respondents familiar with ChatGPT were concerned about the risks it poses to security and safety, according…
Computer scientists at the University of Waterloo have discovered a method of attack that can successfully bypass voice authentication security…
According to @GhostyTongue, a Twitter account sharing exclusive information about the alleged Nickelodeon data leak, two individuals apparently involved in…
As the number of self-driving cars increases, so does the number of cameras on the roads. This creates a possible…
According to @GhostyTongue, a Twitter account sharing exclusive information about the alleged Nickelodeon data leak, two individuals apparently involved in…
We take a look at a change to Google’s Privacy Policy which indicates the use of public data for AI…
Next time you need to track a package, be aware that malicious ads could be leading you to sites that…
The NDIS Quality and Safeguards Commission CIO Michael Kardaris. The Department of Agriculture, Fisheries and Forestry’s assistant secretary of biosecurity…
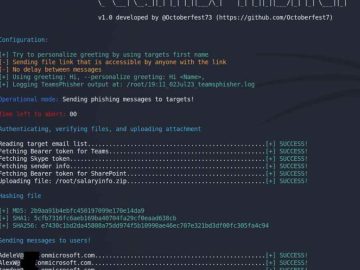
It is getting more difficult to introduce malware into organizations that are being targeted. Many of the conventional payload types,…
RedEnergy is a sophisticated stealer-as-a-ransomware that was employed in attacks targeting energy utilities, oil, gas, telecom, and machinery sectors. Zscaler…