Gareth Heyes | 04 July 2023 at 13:00 UTC As a penetration tester, you need your tools to find the…
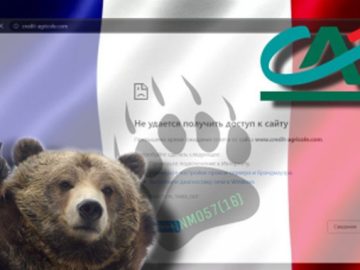
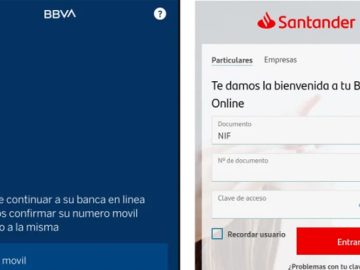
A Mexican threat actor that goes online with the moniker Neo_Net is behind an Android malware campaign targeting banks worldwide….
China is set to put in place export restrictions, in a move that could seriously impact the global semiconductor sector….
By Brett James, Director, Transformation Strategy at Zscaler In recent years, federal agencies have expanded remote work dramatically, and in…
The threat actors behind the DDoSia attack tool have come up with a new version that incorporates a new mechanism…
In this talk, David gives an overview and demo of ZAP’s new heads-up display (HUD), an intuitive and awesome way…
A security researcher and system administrator has developed a tool that can help users check for manifest mismatches in packages…
ChatGPT increases the risk of cyberattacks. By Markus Cserna, CTO, cyan Digital Security The whole world looks with amazement and…
Strategies for Preventing Data Breaches in the Translation Industry By Ofer Tirosh, CEO, Tomedes When it comes to translation, it’s…
Jul 04, 2023Ravie LakshmananCyber Crime / Mobile Security An e-crime actor of Mexican provenance has been linked to an Android…
A service mesh is a layer of IT infrastructure that controls service-to-service communication over a network to enable separate parts…
These tools leverage the advantage that white hat penetration testers have over external attackers: they have access to server binaries/bytecode…