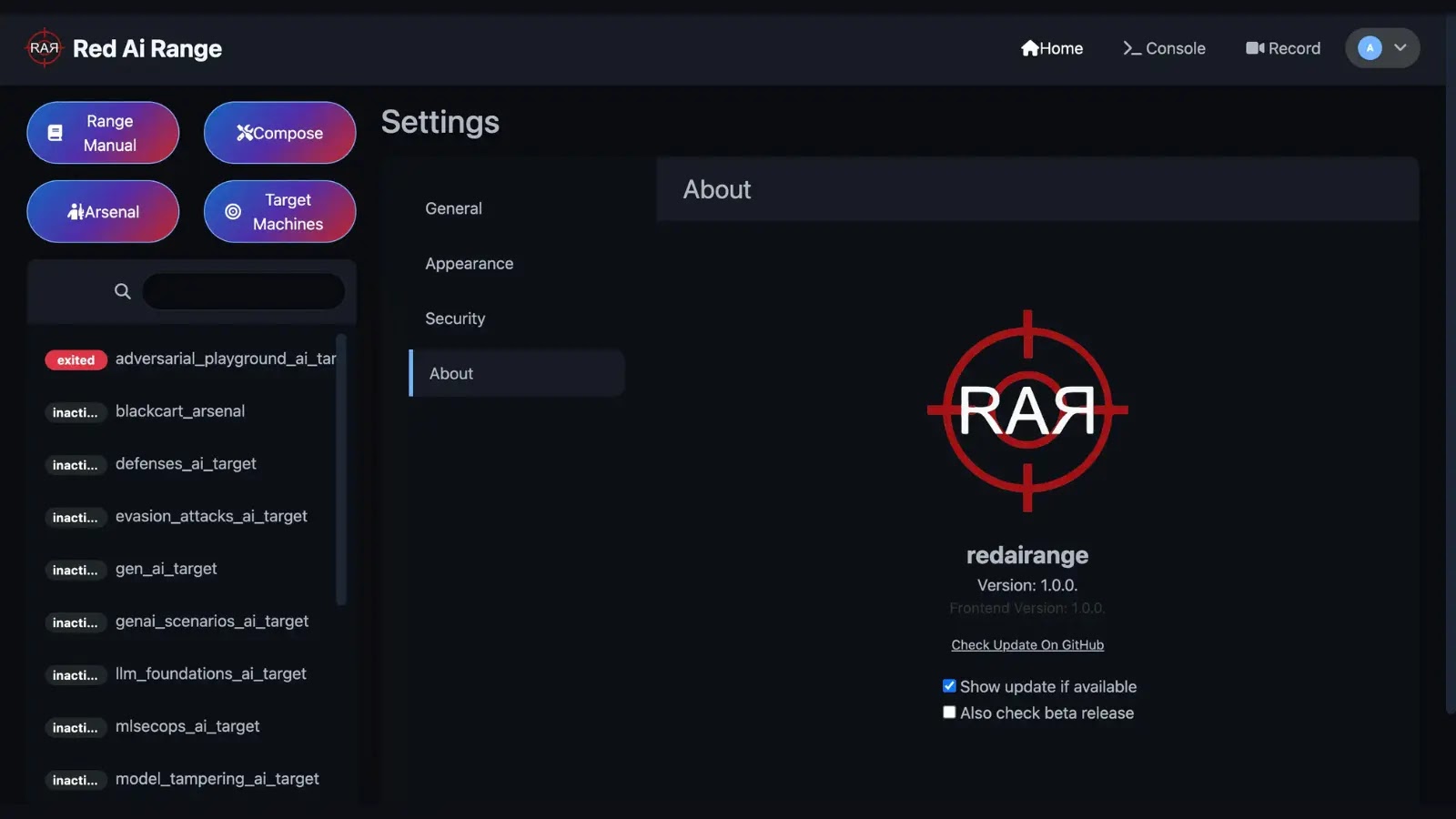
Red AI Range (RAR), an open-source AI red teaming platform, is transforming the way security professionals assess and harden AI…
The financial sector is bracing for a significant shift in its digital landscape as the EU’s Digital Operational Resilience Act…
In 2024, as the Russia-Ukraine war prolongs and military and economic cooperation between North Korea and Russia deepens, cyberspace has…
In today’s digital economy, data is often described as “the new oil” because of its role in fueling artificial intelligence…
New research from Red Canary and Zscaler shows phishing lures now drop RMM tools like ITarian and Atera, giving attackers…
CISOs belong in the Boardroom, according to CrowdStrike (NASDAQ: CRWD) President / CEO and Founder George Kurtz, who reveals the…
Attacks that target users in their web browsers have seen an unprecedented rise in recent years. In this article, we’ll…
China is ramping up its cybersecurity enforcement with new regulations requiring network operators to report severe cybersecurity incidents within one…
The cybersecurity landscape witnessed a significant escalation in July 2025 when the China-aligned threat actor Hive0154, commonly known as Mustang…
Burger King has invoked the Digital Millennium Copyright Act to force the removal of a security researcher’s blog post that…
Taxpayers paid one legal firm double the amount in fees to represent the Post Office in the Horizon scandal statutory…
In April, Rhode Island resident Navah Hopkins received a plea for her help to defeat legislation thousands of miles away…