Researchers at Varonis Threat Labs discovered that some Salesforce sites were improperly deactivated or unmaintained SalesforceGhost Sites. Threat actors can…
In today’s interconnected world, where technology permeates every aspect of our lives, ensuring robust cybersecurity has become an utmost priority….
Jun 02, 2023Ravie LakshmananCyber Espionage / APT U.S. and South Korean intelligence agencies have issued a new alert warning of…
An unnamed vulnerability in MOVEit Transfer has been exploited in the wild and is expected to have caused data breaches….
As per reports, On May 12, 2023, Toyota Motor Corporation discovered that they had been subject to a Potential data…
Here’s a look at the most interesting products from the past week, featuring releases from Bitdefender, ConnectSecure, CYTRACOM, Permit.io, and…
As the world’s most powerful military and economic power, the United States also holds another, less impressive distinction: Cyber threat…
Researchers have identified a critical Google Workspace security issue, which can lead to data exfiltration without leaving a trace. This…
Businesses face significant hazards from ransomware attacks, which are capable of causing severe damage in a brief period. Over the…
Despite rising labor costs, economic inflation, and companies making an effort to cut back, the salary outlook for IT professionals…
Jun 02, 2023Ravie Lakshmanan Zero-Day / Vulnerability A critical flaw in Progress Software’s in MOVEit Transfer managed file transfer application…
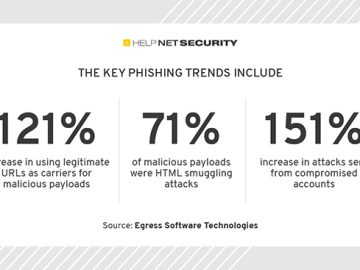
According to Egress, the evolving attack methodologies currently used by cybercriminals are designed to get through traditional perimeter security. “The…