A critical zero-day vulnerability in Progress Software’s enterprise managed file transfer solution MOVEit Transfer is being exploited by attackers to…
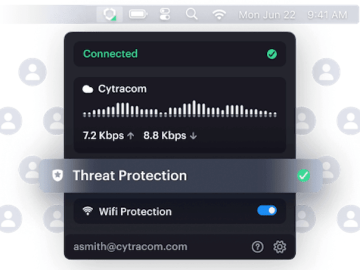
CYTRACOM announces a significant update to its ControlOne platform, enabling MSPs to prevent managed clients from evading security requirements and…
All technology contains bugs. These bugs frequently have security implications that may be exploited by criminals, but are more often…
Hackers are actively exploiting a zero-day vulnerability in the MOVEit Transfer file transfer software to steal data from organizations. MOVEit…
The recent sentencing of two Nigerian nationals, Soloman Ekunke Okpe and Johnson Uke Obogo, yet again has drawn attention to…
The Metropolitan Police Services’ (MPS) director of intelligence has defended the force’s use of facial-recognition technology to a Parliamentary committee,…
Amazon has agreed to pay a fine of $25 million to settle allegations made by the US Federal Trade Commission…
On July 2nd, 2015, HackerOne reached 10,000 valid security vulnerabilities resolved on our platform – that’s 10,000 fewer ways for…
IT hygiene is a security best practice that ensures that digital assets in an organization’s environment are secure and running…
The ways that artificial intelligence (AI) will impact upon our lives are being determined by governments and corporations, with little…
Google Workspace (formerly G Suite) has a weak spot that can prevent the discovery of data exfiltration from Google Drive…
Jun 01, 2023Ravie LakshmananProgramming / Supply Chain Researchers have discovered a novel attack on the Python Package Index (PyPI) repository…