To address a critical vulnerability in the Jetpack WordPress plug-in, Automattic, the company that created the open-source WordPress content management system, has…
ConnectSecure is adding deep attack surface scanning and the Exploit Prediction Scoring System (EPSS) to its cybersecurity platform for managed…
May 31, 2023The Hacker NewsThreat Hunting / Cybersecurity Finding threat actors before they find you is key to beefing up…
With technology progressing at an ever-increasing pace, developers are challenged more than ever to keep code secure and mitigate against…
Bl00dy ransomware group, known for exploiting vulnerabilities in the PaperCut NG software, has claimed its first victim in India, demanding…
The Toyota Motor customer data leak is larger than what was disclosed previously, the company conceded on Wednesday. The latest…
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…
Hiding malicious programs in a computer’s UEFI firmware, the deep-seated code that tells a PC how to load its operating…
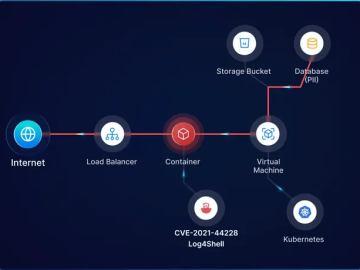
PingSafe launched KSPM module to provide an end-to-end security solution that encompasses the entire container lifecycle, from development to production,…
May 31, 2023Ravie LakshmananEndpoint Security / Vulnerability Microsoft has shared details of a now-patched flaw in Apple macOS that could…
Panasas’s recent announcement of the addition of an edge platform to its family of scale-out NAS came alongside a planned…
Cyber espionage group ‘Strontium Stealer’ has launched a Remote Access Trojan (RAT) ‘LithiumRAT’ packed with new features to enhance malware…