The best hackers use their creativity to find vulnerabilities. They are not bound to the vulnerability types that they already…
NoName hackers attacked Lithuania, as their DDoS attacks continue. Among the victims are the e-services of the Seimas, Lithuania’s parliament,…
May 30, 2023Ravie LakshmananMobile Security / Android A new open source remote access trojan (RAT) called DogeRAT targets Android users…
Hacker cinema from the 1990’s upon original release was criticized as being “dubious,” “unrealistic,” and “implausible.” Blast ahead 20 years…
We recently launched the Hack The World competition to challenge you all to find as many vulnerabilities as possible over…
Following the MCNA data breach, for which hacker group LockBit demanded a ransom amount of $10 million, the U.S.-based government-sponsored…
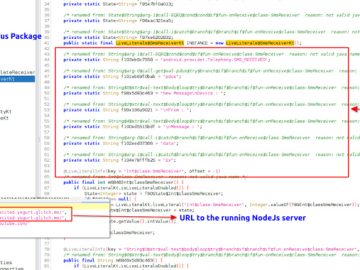
Python Package Index (PyPI) has been used by several developers worldwide for creating a project or installing any other dependencies…
MCNA, also known as Managed Care of North American Dental, has issued a statement on its website regarding a data…
Transparency between hackers and security teams is vital to a successful bug bounty program. The “front door” for hackers to…
Google recently released new top-level domains (TLDs) like .dad, .phd, .mov, and .zip, raising concerns within the security community due…
HackerOne kicked off its inaugural H1-702 live hackathon in Las Vegas. Across three nights, Hackers worked with Zenefits, Snapchat and…
Building a custom cracking rig for research can be expensive, so penetration tester Max Ahartz built one on AWS. In…