As a hacker, you know the best security bugs you reported to each program: the epic find in a popular…
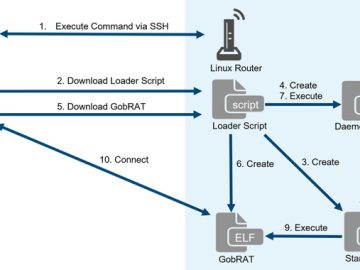
May 29, 2023Ravie LakshmananLinux / Network Security Linux routers in Japan are the target of a new Golang remote access…
It’s time for the third installment of Top 5 Vulnerability Reports on HackerOne. What a quarter! We sweated through the…
As part of the ongoing operation ‘OpColombia’, the hackers of the SeigedSec group added two more targets to their victim…
This first appeared in the San Francisco Business Times on November 3, 2016. View the original article here: http://www.bizjournals.com/sanfrancisco/news/2016/11/03/marten-mickos-hackerone-hackers-bugs-bounties.html Marten…
A new phishing technique called “file archiver in the browser” can be leveraged to “emulate” a file archiver software in…
Communication is one of the keys to success in running a bug bounty program. From facilitating more than 650 bug…
It is largely recognised among the IT security community that there is a direct correlation between the quality of code…
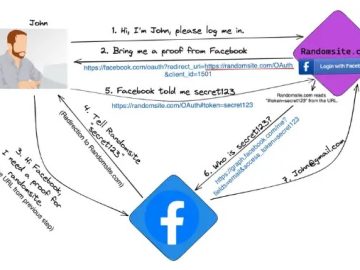
OAuth is the modern authentication mechanism most applications use to ease off the signing by creating a cross-allow application access…
NoName DDoS attacks have been a clear and present threats to pro-Ukraine nations for a year. This time, the Pro-Russian…
Today, Secretary of the Army, Eric Fanning, announced plans to launch the U.S. Army’s first ever bug bounty challenge in…
Google recently fixed a critical Cloud SQL database service flaw that could have been exploited to access sensitive data and…