A Tesla employee has reportedly stole about 100GB of data related to the automaker and handed it over to a…
With hacker-powered security, it’s critical to open and maintain a line of communication with the hackers who are working to…
Firefox users have been complaining about very intrusive full-screen advertisements promoting Mozilla VPN displayed in the web browser when navigating an…
Insider threats are a growing phenomenon, but many businesses aren’t yet doing enough to protect themselves effectively. In Europe and…
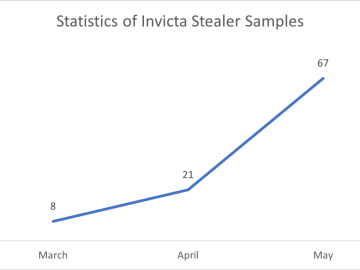
Researchers spotted a new infostealer, dubbed ‘Invicta Stealer’, being promoted by its developer on Facebook, leveraging the social media platform…
Image: Bing Image Creator Emby says it remotely shut down an undisclosed number of user-hosted media server instances that were recently…
Birmingham City Council’s new council leader has informed local newspapers of spiralling costs in a major enterprise resource planning (ERP)…
To learn more about how legal teams and federal enforcers view hacker-powered security, we invited Megan Brown, partner, and Matthew…
The city of Augusta in Georgia, U.S., has confirmed that the most recent IT system outage was caused by unauthorized access…
Security researchers have shared a deep dive into the commercial Android spyware called Predator, which is marketed by the Israeli…
In January 2016, the Tor Project launched its first private bug bounty program on HackerOne. Today the Tor Project announced…
5G is a game changer for mobile connectivity, including mobile connectivity to the cloud. The technology provides high speed and…