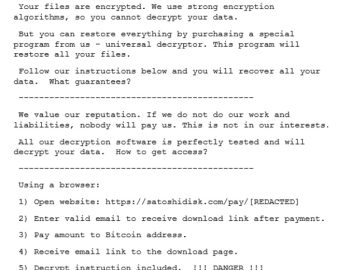
Nokoyawa Leaks, the official communication channel for the Nokoyawa ransomware group, re-emerged on the darkweb this week, revealing a list…
NVIDIA’s market value is set to soar to an impressive $1 trillion by the end of this year, driven by…
Perception Point’s team has identified a 356% increase in the number of advanced phishing attacks attempted by threat actors in…
Hackers, we have some great news to share! We’re happy to announce that we’re adding Bank Transfers as a payout…
The impact of AI technology on our lives is a complex and multifaceted topic. It has the potential to bring…
Here’s a look at the most interesting products from the past week, featuring releases from Axiado, Delinea, Netscout, Radware, and…
A newly identified ransomware operation has refashioned leaked LockBit and Babuk payloads into Buhti ransomware, to launch attacks on both…
Intro Recon plays a major role while hacking on a program. Recon doesn’t always mean to find subdomains belonging to…
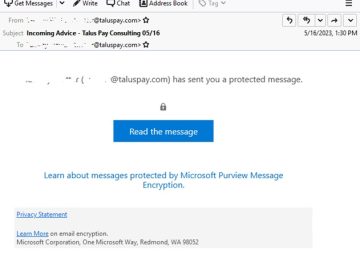
Phishers are using encrypted restricted-permission messages (.rpmsg) attached in phishing emails to steal Microsoft 365 account credentials. “[The campaigns] are…
May 26, 2023Ravie LakshmananEmail Security / Zero-Day Email protection and network security services provider Barracuda is warning users about a…
Our Hacker-Powered Security Report is so chock-full of compelling insights, interesting tidbits, and surprising stats that we decided to distill…
Cybercriminals are increasingly posing as multi-factor authentication vendors and small businesses are becoming more popular targets, according to VIPRE. Attachment-based…