An 18-year-old Wisconsin teenager has been accused by federal authorities of a cyberattack that compromised 60,000 user accounts at the…
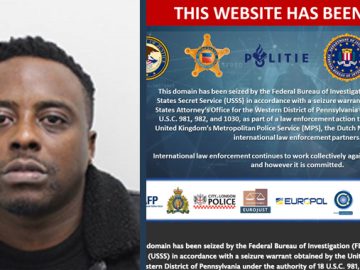
At the peak of its illicit activities, iSpoof enabled scammers to contact nearly 20 individuals every minute, employing false identities…
It’s no secret that data leaks have become a major concern for both citizens and institutions across the globe. They…
Snatch ransomware has attacked medical societies in the US and Canada, claimed the threat actor. The Medical Society of the…
Cross-site scripting (XSS) is a type of attack that can be carried out to compromise users of a website. The…
“We know that there’s a problem within the cybersecurity industry when it comes to burnout – and it’s a problem…
According to reports from the FSB (Federal Security Service) Department’s Press Service in Rostov Region, Yevgeny Kotikov, an IT specialist,…
The more the world gets hacked, the more we need hackers. We need white hats. They will find vulnerabilities so…
Router vulnerability, in both industrial and consumer units, has been a preferred attack point for hackers. Researchers have published alerts…
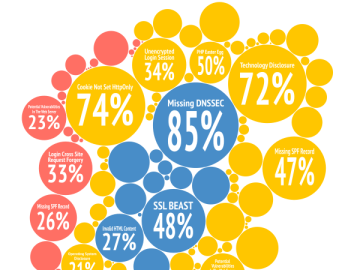
What do typical websites look like through the eyes of our vulnerability scanner the first time they are tested? How does…
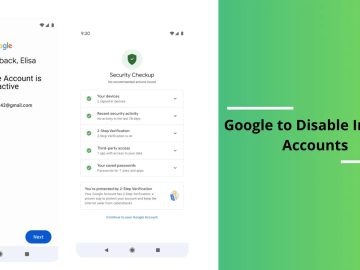
Google amended its “inactive account policy” on Tuesday and will now remove accounts that haven’t been used or registered for…
May 22, 2023Ravie LakshmananCyber Crime / Hacking A U.K. national responsible for his role as the administrator of the now-defunct…