OpenAI officially announced the release of an official iOS app that gives users access to its well-known AI chatbot on the…
The web-based user interface of some Cisco Small Business Series Switches contains multiple vulnerabilities, according to a warning from Cisco….
A threat actor with a history of targeting Microsoft servers has recently gained control over virtual machines (VMs) and installed…
Hacktivity can save your company. Take help from hackers. You can’t do it alone. Approach hackers with an assumption of…
In today’s digital age, profit-making organizations across industries are increasingly reliant on technology and the internet to conduct their operations….
Insecure Direct Object Reference allows attackers to manipulate references to gain access to unauthorized data. A proof of concept video follows…
May 19, 2023Ravie LakshmananZero-Day / Endpoint Security Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS,…
Here’s a look at the most interesting products from the past week, featuring releases from Bitwarden, Cloudflare, ComplyAdvantage, Enzoic, Neurotechnology,…
In the last two parts of this series, we discussed the AWS Shared Responsibility Model. We started with keeping your…
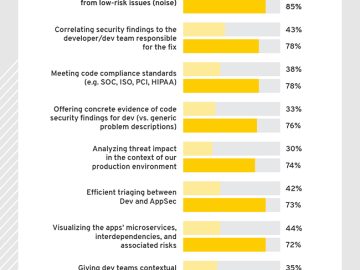
AppSec teams are stuck in a catch-up cycle, unable to keep up with the increasingly rapid, agile dev pace, and…
We’ve got some cool events coming up and we’re looking forward to discussing security at tech conferences, meetups and webinars. Check…
DDoS attacks appear to reflect major geo-political challenges and social tensions and have become an increasingly significant part in the…