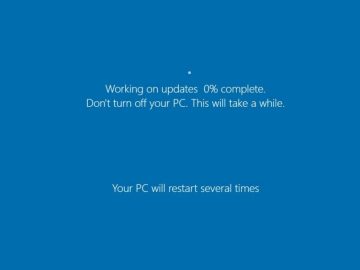
When the fake Windows update UI is launched, the victim believes it to be a legitimate software update process where…
By , Co-Founder and CEO at Software supply chain compromises have been top-of-mind for CISOs and their security teams for…
Jul 12, 2023THNRansomware / Cyber Threat Ransomware has emerged as the only cryptocurrency-based crime to grow in 2023, with cybercriminals…
A whistleblower is contacting NatWest customers affected by a data breach which has forced her to store the sensitive information…
Microsoft reported on Tuesday that a Chinese cyberespionage group it tracks as Storm-0558 was recently spotted using forged authentication tokens…
A Chinese hacking group has breached the email accounts of more than two dozen organizations worldwide, including U.S. and Western…
The Russian intelligence-backed advanced persistent threat (APT) group known variously as APT29, Nobelium or Cozy Bear, arguably most famous for the…
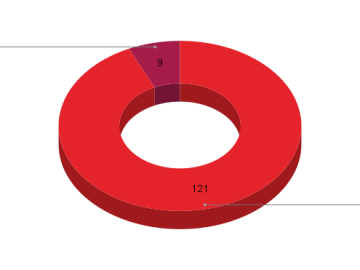
The Microsoft Patch Tuesday for July addressed 132 vulnerabilities as reports of zero-day exploitation surface in the media. Out of…
Implementing an AWS multi-account strategy is a popular approach that helps organizations to manage their cloud resources efficiently. In my…
Since late last month, a Russian cyber-extortion gang has been exploiting a flaw in a widely used software known as…
Microsoft announced it has mitigated a cyber attack by a China-linked threat actor, tracked as Storm-0558, which targeted customer emails….
Image: Bing Create Data from the first half of the year indicates that ransomware activity is on track to break…