The moment a cyberattack strikes, the clock starts ticking. Files lock up, systems stall, phones light up and the pressure…
Samsung has released its September 2025 security update, addressing a critical zero-day vulnerability that is being actively exploited in the…
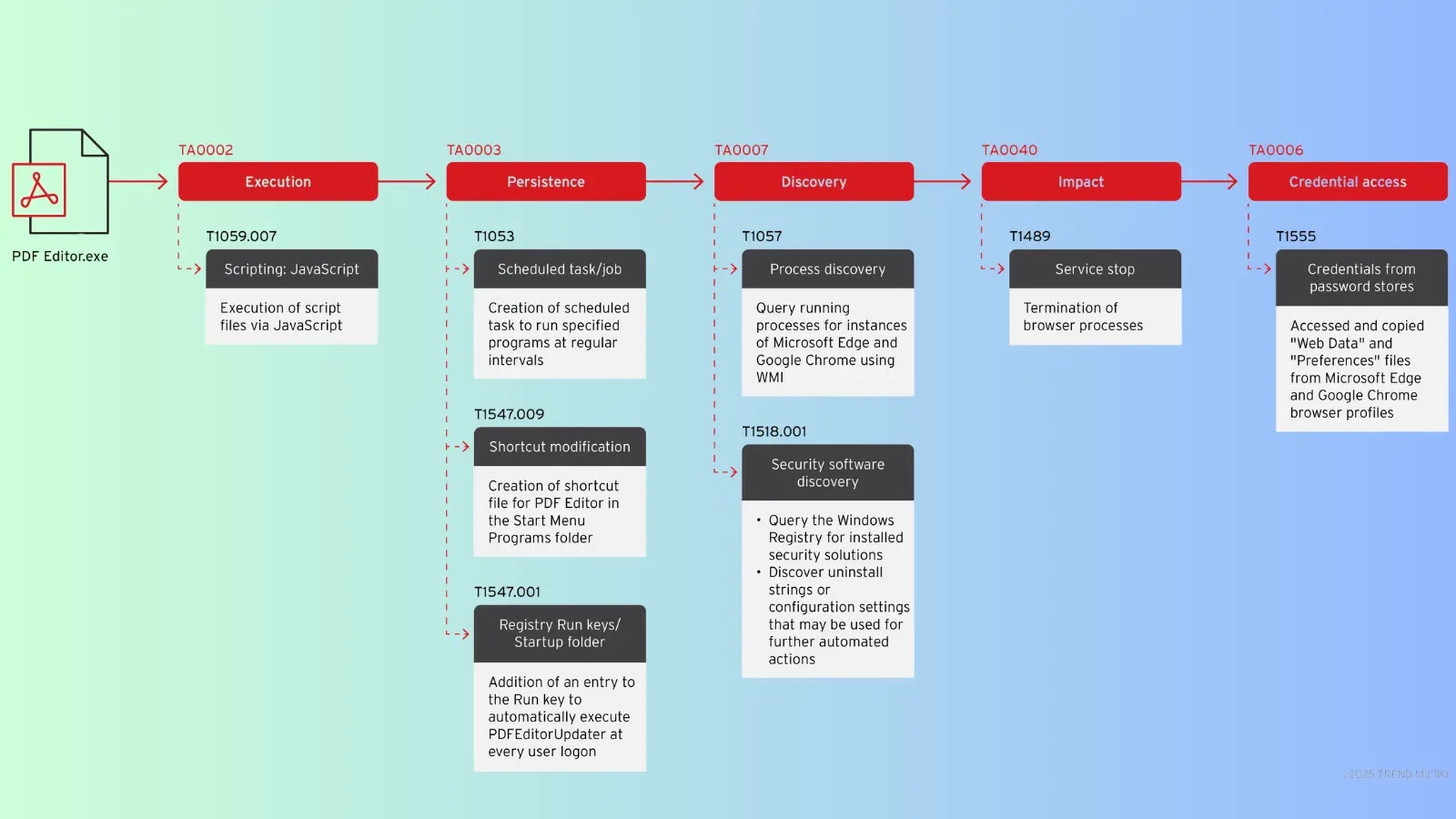
EvilAI, a new malware family tracked by Trend Research, has emerged in recent weeks disguised as legitimate AI-driven utilities. These…
Debojyoti ‘Debo’ Dutta admits that his deep domain experience means he is just “a little biased” when it comes to…
Apple in early September sent a fresh wave of threat notifications to French users it believes might have been targeted…
WebAssembly is a low-level assembly language that can process binary formats on the web. It runs on the web but…
Within mere hours of its public unveiling, the K2 Think model experienced a critical compromise that has sent ripples throughout…
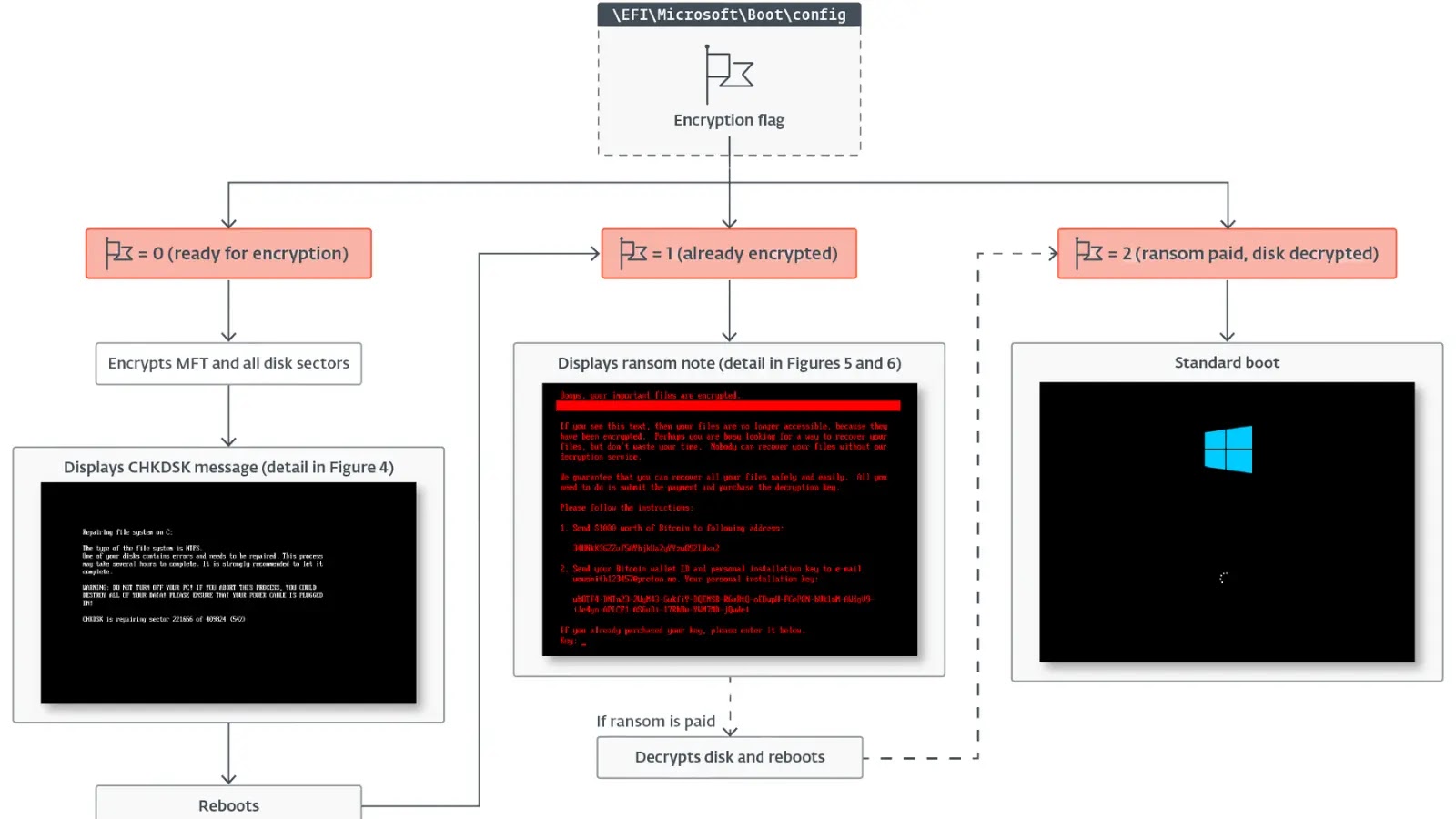
ESET Research has uncovered a sophisticated new ransomware variant called HybridPetya, discovered on the VirusTotal sample sharing platform. This malware…
Sep 12, 2025Ravie LakshmananVulnerability / Cyber Espionage The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical…
A TechUK report that claimed datacentres in England use less water than previously thought has been accused of containing “methodological…
Threat actors are exploiting a critical-severity vulnerability in DELMIA Apriso factory software, the US cybersecurity agency CISA warns. Developed by…
Amelia Coen | 12 September 2025 at 12:21 UTC Arman S., a full-time independent security researcher and bug bounty hunter,…