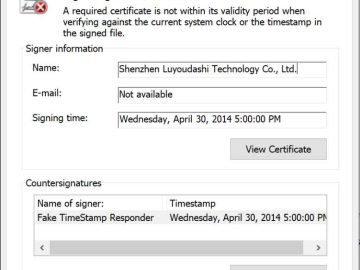
Chinese-speaking threat actors have been shown to be using a Microsoft Windows policy vulnerability to spoof signatures on kernel-mode drivers….
“The Legion” is a Python-based software that has been crafted with the explicit intention of gathering credentials. Its propagation initially…
For July 2023 Patch Tuesday, Microsoft has delivered 130 patches; among them are four for vulnerabilites actively exploited by attackers,…
The US today announced the arrest of Shakeeb Ahmed on charges related to the defrauding of a decentralized cryptocurrency exchange…
Microsoft has released the mandatory Windows 11 22H2 KB5028185 cumulative update to fix security vulnerabilities, enable the new Moment 3…
Microsoft has taken another step towards security which has revolutionized the way security professionals use Microsoft 365 Defender across devices…
Nearly ten years ago, the sprawling dark web drug market known as the Silk Road was torn offline in a…
Rekoobe is a notorious backdoor that primarily targets Linux environments, and it’s actively exploited by the threat actors, mainly a…
The “team” behind Genesis Market is advertising the sale of its source code and database on a hacker forum, expressing…
Russian spies and cybercriminals are actively exploiting still-unpatched security flaws in Microsoft Windows and Office products, according to an urgent…
Microsoft disclosed today an unpatched zero-day security bug in multiple Windows and Office products exploited in the wild to gain…
SAP has released their updates for patch day of this month, in which several vulnerabilities have been fixed and CVEs…