Geacon, a Cobalt Strike implementation written in Golang, is likely to attract the attention of threat actors looking for vulnerable…
It’s been over a year since Grammarly launched its first bug bounty program on HackerOne. It’s been a private, invite-only…
The ‘RA Group’ is a recently emerged ransomware organization that is actively attacking the following companies in the United States…
Scientists from Russia, working for Don State Technical University, have developed a new medium of communication through the technology of…
Unvalidated redirects and forwards, also referred to as Open Redirect, is featured on OWASP‘s list of the ten most common vulnerabilities….
Cybercriminals are starting to target Microsoft’s VSCode Marketplace, uploading three malicious Visual Studio extensions that Windows developers downloaded 46,600 times….
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
Neurotechnology announced the expansion of the MegaMatcher product line with the release of the MegaMatcher Identity Management System (IDMS). The…
GitLab is a single application for the entire DevOps lifecycle, making software development easier and more efficient, without sacrificing security…
May 17, 2023Ravie LakshmananCyber Threat / Mobile Security A hacking group dubbed OilAlpha with suspected ties to Yemen’s Houthi movement…
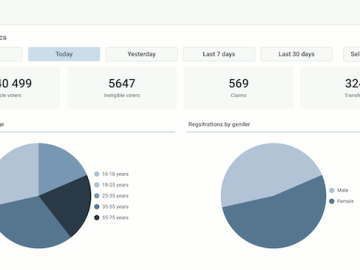
Running an e-commerce site does not only require plenty of business savvy, but also a great deal of security awareness….
Technology provider ScanSource has announced it has fallen victim to a ransomware attack impacting some of its systems, business operations, and…