IBM acquired Polar Security reportedly for a reported amount of $60 million to integrate automated cloud management for its clients….
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…
There’s no such thing as a free lunch. Nor is there such a thing as a free TV. But Telly…
The pervasive influence of Artificial Intelligence (AI) is propelling a remarkable wave of transformation across diverse sectors. As AI technologies…
May 17, 2023Ravie LakshmananInternet of Things / Vulnerability The second generation version of Belkin’s Wemo Mini Smart Plug has been…
With enough hackers, all security vulnerabilities are shallow. There is no better way to know the level of security of…
IBM has made a smart move to address the issue of cloud data protection by acquiring Polar Security, a company…
Our schedule for the autumn and winter is quickly filling up and we’re looking forward to all the awesome events we’ll…
Any major trend or world event, from the coronavirus pandemic to the cryptocurrency frenzy, will quickly be used as fodder…
Sophos researchers uncovered multiple apps masquerading as legitimate, ChatGPT-based chatbots to overcharge users. These apps have popped up in the…
ServiceNow CEO Bill McDermott called for IT and the business to come together for a new future in what he…
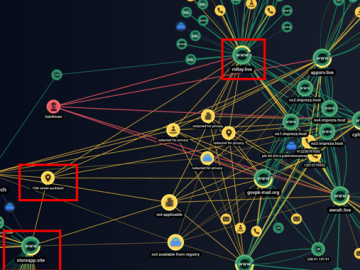
May 17, 2023Ravie LakshmananCyber Espionage / Threat Intel Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific…