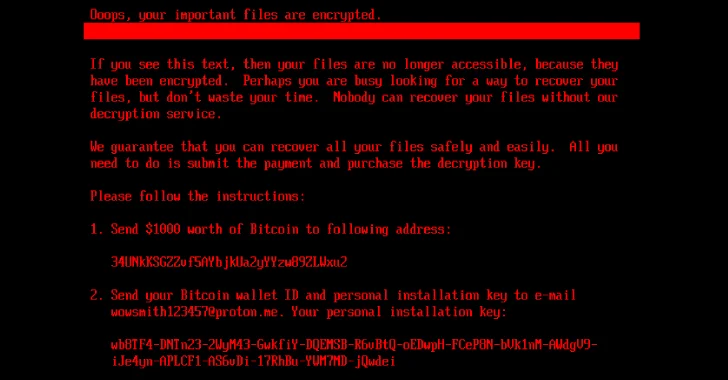
In late July 2025, a series of ransomware samples surfaced on VirusTotal under filenames referencing the notorious Petya and NotPetya…
It’s common knowledge in the cybersecurity industry that ransomware is on the rise, with median demands rising 20% year-over-year across…
Microsoft has released security advisories for four newly discovered vulnerabilities in its Windows Defender Firewall Service that could enable attackers…
Cybersecurity is an industry brimming with top experts bringing deep domain and subject matter expertise on everything from cybercrime, to…
The US Cybersecurity and Infrastructure Security Agency (CISA) has affirmed its continuing support for the Common Vulnerabilities and Exposures (CVE)…
Cybersecurity researchers have discovered a new ransomware strain dubbed HybridPetya that resembles the notorious Petya/NotPetya malware, while also incorporating the…
Sainsbury’s CEO Simon Roberts, Wickes chief David Wood, and Fortnum & Mason boss Tom Athron were among the executives to…
Amelia Coen | 12 September 2025 at 12:21 UTC Arman S., a full-time independent security researcher and bug bounty hunter,…
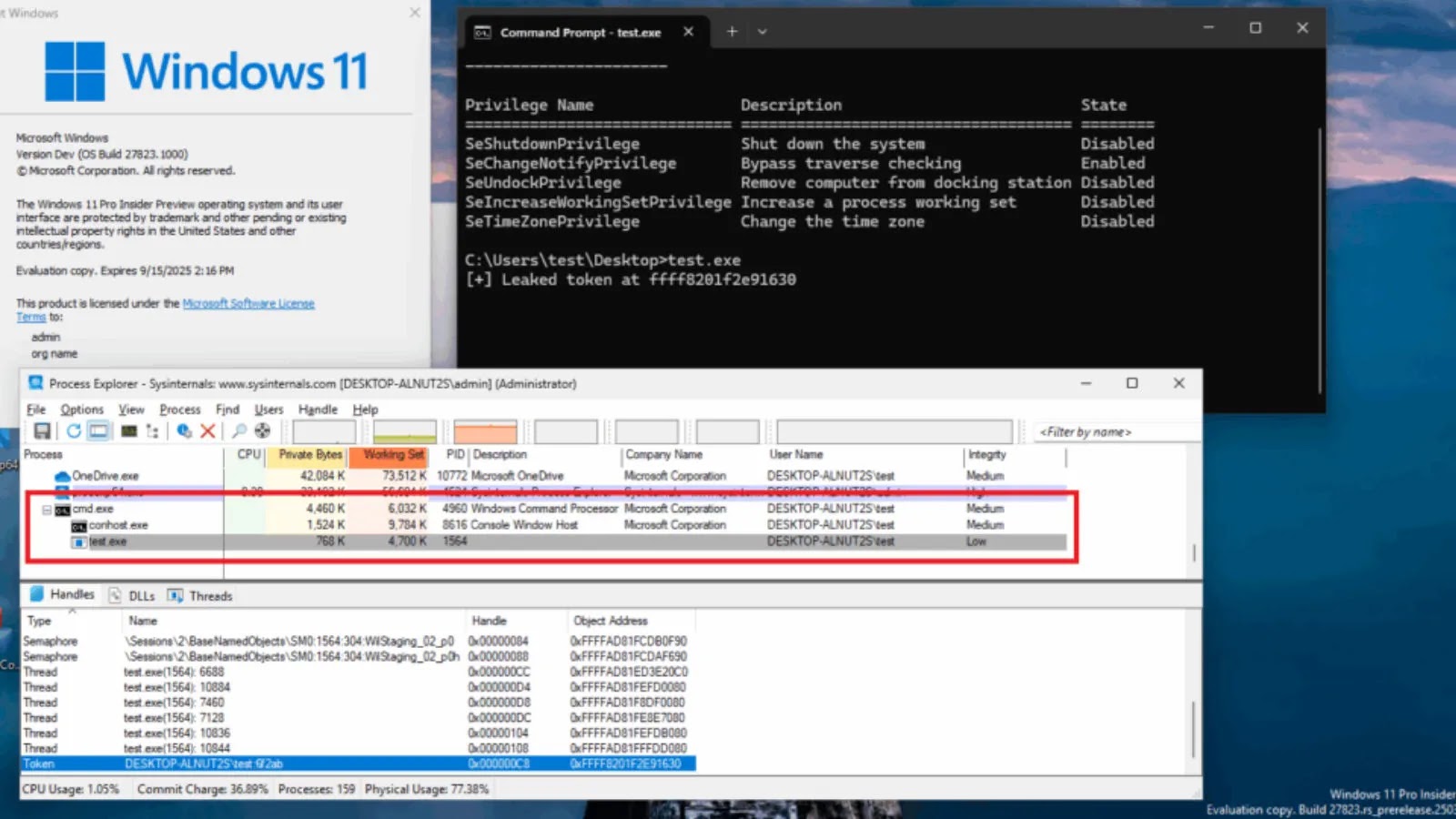
A new kernel address leak vulnerability has been discovered in the latest versions of Windows 11 (24H2) and Windows Server…
A malicious ISO image named Servicenow-BNM-Verify.iso was uploaded to VirusTotal from Malaysia with almost no detections. The image contains four…
Scattered Lapsus$ Hunters, linked to the Jaguar Land Rover cyberattack, claims to shut down as experts suggest the group is…
The flow and ebb of international supply chains is far from new, with the grand medieval churches of the Cotswolds…