In March 2023, Group-IB’s Threat Intelligence team accessed the Qilin ransomware (Agenda ransomware) group and discovered that it is a…
The crawler is the heart of the Detectify service. During the crawling phase, Detectify is trying to collect all possible…
As ransomware attacks continue to wreak havoc on organizations worldwide, many official standards and regulations have been established to address…
The Insurance industry was the most targeted sector in Q1, 2023, according to Indusface’s State of Application Security report, with…
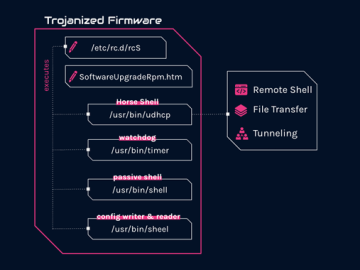
A Chinese state-sponsored hacking group named “Camaro Dragon” infects residential TP-Link routers with a custom “Horse Shell” malware used to…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
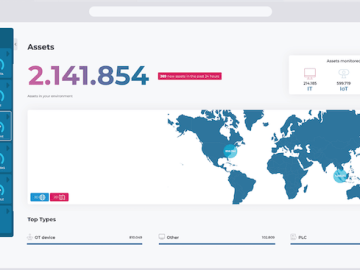
Nozomi Networks has introduced Vantage IQ, the AI-based analysis and response engine designed to address security gaps and resource limitations…
The domain name system (DNS) which enables any computer on the internet to be identified in a human-readable form, is…
When hackers participate in programs on the HackerOne platform, they agree to help empower our community by following the HackerOne…
The U.S. Justice Department has filed charges against a Russian citizen named Mikhail Pavlovich Matveev (also known as Wazawaka or…
If you browse online news sources covering San Francisco, it’s evident that there is a recurring theme of articles highlighting…
May 16, 2023Ravie LakshmananNetwork Security / Threat Intel The Chinese nation-state actor known as Mustang Panda has been linked to…