As soon as WordPress launch a new version they publish a changelog on their website where you can find what…
The information-stealing malware market is constantly evolving, with multiple malware operations competing for cybercriminal customers by promoting better evasion and…
The Philadelphia Inquirer daily newspaper is working on restoring systems impacted by what was described as a cyberattack that hit…
Based on the recent report from char49, it appears that there was a critical flaw in Ferrari’s subdomain, which led…
What’s your favorite T-shirt? Maybe one from that conference you went to 5 years ago, a sleek threadless tee, or…
In March, the Zero Day Initiative (ZDI) organized a competition called “Pwn2Own.” Several vulnerabilities were discovered during this event across…
Many are most likely already familiar with CDNs, Content Delivery Networks, but in short, a CDN is a service where…
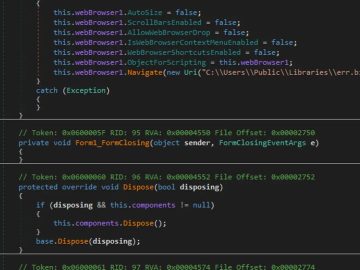
eSentire TRU (Threat Response Unit) has recently discovered a scamming activity conducted via a fake QuickBooks installer that sends a…
CRIL discovered a recently identified ransomware group called BlackSuit, which poses a threat to users of both widely used operating…
Elmore says the goal is to force reform. “We can’t bring the victims of this lawsuit back, but we can…
Continuous improvement is at our heart, and the Hacker Dashboard is an excellent example of how we’ve been iterating based…
Google has added support for more scripting languages to VirusTotal Code Insight, a recently introduced artificial intelligence-based code analysis feature….