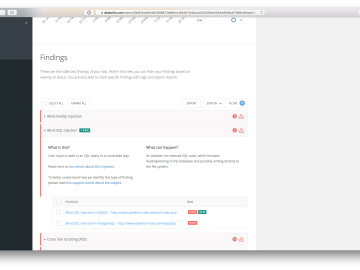
1) More transparency on what tests we have performed Transparency is one of our core values at Detectify, and we…
The UK’s National Cyber Security Centre (NCSC), and the Information Commissioner’s Office (ICO), have banded together to urge those affected…
Toyota Motor Corporation disclosed a data breach on its cloud environment that exposed the car-location information of 2,150,000 customers for…
The cybersecurity researchers at Akamai recently affirmed as web applications and third-party tools become more prevalent, the risk of cyber-attacks…
Researchers from Trend Micro at Black Hat Asia claim that criminals have pre-infected millions of Android devices with malicious firmware…
May 12, 2023Ravie LakshmananNetwork Security / Malware As many as five security flaws have been disclosed in Netgear RAX30 routers…
Prior to attending Hacker Summer Camp, there were whispers (or roars) of the infestation of grasshoppers in Las Vegas, Nevada….
HM Revenue & Customs (HMRC) is being applauded for its “pragmatic” approach to conducting an 18-month IR35 compliance check on…
Assign severity to policy breaches AppSec teams often struggle to either validate or scale their security policies, like enforcing security…
May 12, 2023Ravie LakshmananLinux / Malware A previously undocumented and mostly undetected variant of a Linux backdoor called BPFDoor has…
The Play ransomware group has leaked 5GB of pilfered data allegedly from the City of Lowell cyber attack. The official…
It’s been two years since Upserve launched its public bug bounty program on HackerOne. During that time, Upserve’s security team…