Mar 20, 2023Ravie LakshmananEndpoint Security / Email Security The notorious Emotet malware, in its return after a short hiatus, is…
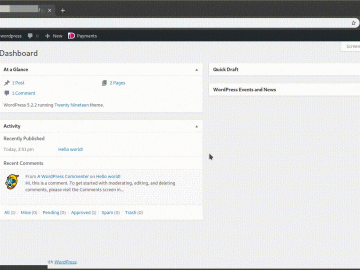
Proof of concept BackgroundWith a 60% market share WordPress is the most used CMS at this moment. Out of the…
Alexander and others have been examining the claims made so far. The New York Times and Die Zeit both published stories on…
After the release of ChatGPT in November 2022, the OpenAI CEO and the people behind the conversational chatbot launch say…
Our reliance on face matching for identity verification is being challenged by the emergence of artificial intelligence (AI) and facial…
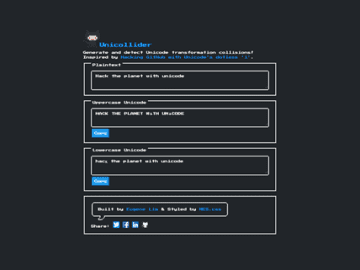
Plus a tool and tips for defenders. In this article, I will describe how Unicode — the encoding standard behind…
As a result of a recent data breach, the NBA notified all its fans about the fact that a significant…
99% of all businesses across the United States and Canada are mid-sized businesses facing cybersecurity challenges, according to a Huntress…
Hello Everybody, Welcome to my FIRST writeup! Just to give you some background, My name is Daniel, I started hacking…
This week wasn’t about me. I and millions of others were focused on the murder of George Floyd. Black Lives Matter. My progress…
Capture the flag events are particular fun events done to challenge people and get people to really think about the…
Easy Bugs for Hard Cash Continue reading on Medium » Source link