Although networks, systems, and cyber security have come on in leaps and bounds, the fundamental theories of access control and…
Just five years ago, leading rideshare, food delivery, and payments company Grab, became one of the first companies in…
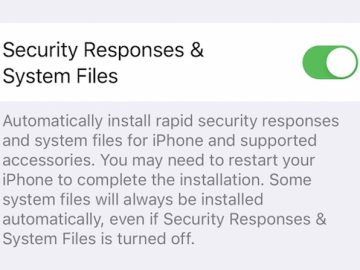
The security updating of iPhones, iPads and Macs has entered a new stage: Apple has, for the first time, released…
Thank you for joining! Access your Pro+ Content below. 2 May 2023 The ethics of military AI Share this item…
On February 20th, Drupal released a security update that fixes a critical remote code execution vulnerability. Detectify scans your site…
The TechTarget/Computer Weekly IT Priorities 2023 survey found that 41% of IT decision-makers expect to increase their IT spending this…
But they had been at it only 24 hours when they found the passage they’d been looking for: a single…
The NextGen Healthcare cyber attack story continues, with the company disclosing another cyber incident in a regulatory filing. The disclosure…
Royal Ransomware Group has continued its ransomware attacks targeting critical infrastructure sectors, including healthcare, communications, and education. The Montana State…
Imagine being part of an organization that has a security team that manages risks by saying “no” to change in…
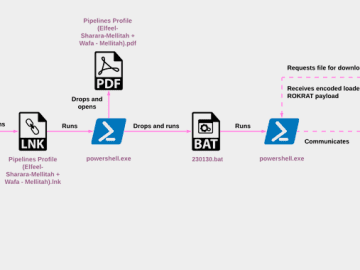
May 02, 2023Ravie LakshmananThreat Intelligence The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as…
With days to go until the coronation of King Charles III, cyber fraudsters are seeking to capitalise on a surge…