Whether cloud migration is a cause or effect of digitalization, it is nevertheless a major part of the journey currently…
Aaron Bray, Co-Founder and CEO of A few weeks ago, PyPI announced that it temporarily disabled the ability for users…
Jun 21, 2023Ravie LakshmananCyber Threat / Privacy The North Korean threat actor known as ScarCruft has been observed using an…
Russian anti-malware vendor Kaspersky has analyzed the spyware implant deployed as part of recent zero-click iMessage attack that targeted iOS-powered…
Allegedly, the satellite in question is purportedly owned by Maxar Technologies, a prominent US-based space technology firm, while it has…
[ This article was originally published here ] A way to manage too much data To protect the business, security…
After years of breakneck growth, China’s security and surveillance industry is now focused on shoring up its vulnerabilities to the…
The Federal Trade Commission (FTC) says Amazon allegedly used dark patterns to trick millions of users into enrolling in its…
As an AI language model like ChatGPT, you cannot directly earn money. However, there are a few ways you can…
Web application security firm Defiant warns of critical-severity authentication bypass vulnerabilities in two WordPress plugins with tens of thousands of…
Researchers discovered a new strain of malware called Condi that targets TP-Link Archer AX21 (AX1800) Wi-Fi routers. Fortinet FortiGuard Labs Researchers discovered a…
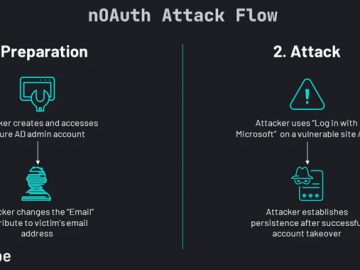
Jun 21, 2023Ravie LakshmananAuthentication / Vulnerability A security shortcoming in Microsoft Azure Active Directory (AD) Open Authorization (OAuth) process could…