RSA Conference 2023 is taking place at the Moscone Center in San Francisco. Check out our microsite for the conference…
Apr 26, 2023Ravie Lakshmanan The prolific Iranian nation-state group known as Charming Kitten targeted multiple victims in the U.S., Europe,…
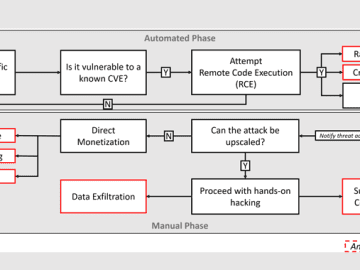
Security researchers at managed detection and response (MDR) specialist eSentire have revealed how they are turning the tables on an…
Cybersecurity experts have discovered that a threat actor is selling a new information-stealing malware called Atomic macOS Stealer (AMOS) on…
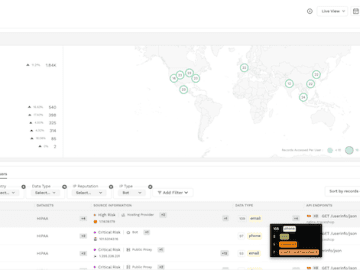
For TikTok, a platform that sees more than one billion monthly active users, staying ahead of cyber threats is always…
Today, Keeper Security announced it has been named an Overall Leader in the 2023 Leadership Compass- Secrets Management report by global…
RSA Conference 2023 is taking place at the Moscone Center in San Francisco. Check out our microsite for the conference…
Greetings, digital guardians. Today, we’ll be diving into the wonderful world of External Attack Surface Management (EASM) platforms. As the…
In the recent hybrid, multi-vendor, multi-threat world, Cisco Extended Detection and Response (XDR) streamlines security operations with unrivaled visibility across…
Traceable AI launched Zero Trust API Access to help organizations better protect sensitive data, stop API abuse, and align data…
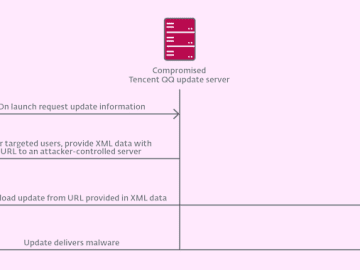
Apr 26, 2023Ravie LakshmananCyber Threat / APT Group The advanced persistent threat (APT) group referred to as Evasive Panda has…
To tie in with the government’s new Business Connect UK innovation and growth conference, prime minister Rishi Sunak has announced…