Apr 26, 2023Ravie LakshmananVirtual Machine / Cybersecurity VMware has released updates to resolve multiple security flaws impacting its Workstation and…
Anonymous Sudan Targets US Hospitals: Within 24 hours of making the disclosure on its Telegram Page, Anonymous Sudan began targeting…
Created/Updated: August 21, 2022 The internet’s gone a bit crazy about Sam Harris supposedly supporting censorship. As in most cases,…
Among the topics they explored included the success of their long-running bug bounty programs in discovering security vulnerabilities, how to…
Artificial intelligence (AI) is a buzzword that has gained significant traction over the past decade. Many experts predict that AI…
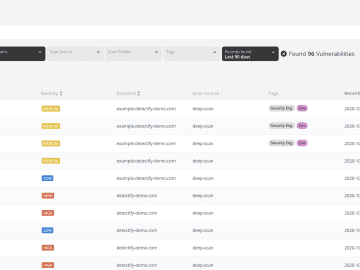
Triage is just as important to security teams as it is to hospital workers. Now, you can prioritize and remediate…
Google Authenticator was launched in 2010, which provides additional security for various applications by providing authentication codes for every sign-in….
The Quad nations comprising India, Japan, Australia, and the United States will reach an agreement on how to create a…
A study conducted among CISOs worldwide from various industries sheds light on their strategies amid a challenging threat environment, identifies…
Midjourney is like using a Mac, and DALL-E is like using the Linux command line Created/Updated: August 21, 2022 Created…
In this Help Net Security interview, Eve Maler, CTO at ForgeRock, talks about how digital identities continue to play a…
The Cybersecurity & Infrastructure Security Agency (CISA) published a report alerting about DoS attacks that can be launched by exploiting…