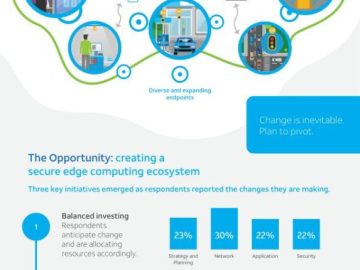
Today, HackerOne published The 2022 Attack Resistance Report: A HackerOne Security Survey. Our research revealed an increasing gap—the attack resistance…
Attackers are exploiting severe vulnerabilities in the widely-used PaperCut MF/NG print management software to install Atera remote management software to…
At RSA Conference 2023, the key theme for Mend is automation. Their focus is on helping people put their application…
Detectify is honored to start off the RSA 2023 Conference with the news that it has been recognized as the…
KuCoin’s Twitter account was hacked, allowing attackers to promote a fake giveaway scam that led to the theft of over…
[ This article was originally published here ] AT&T Cybersecurity is committed to providing thought leadership to help you strategically…
Corporate IT teams have expressed discomfort towards the use of employee surveillance technologies at work, with both workers and managers…
Can you imagine Hard Disk Drives (HDD) and Solid-State Disks (SSD) being immune to ransomware attacks? Well, a company named…
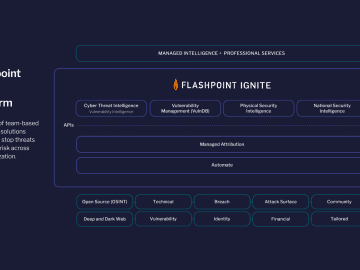
Flashpoint has released Ignite, a new intelligence platform that accelerates cross-functional risk mitigation and prevention across CTI, vulnerability management, national…
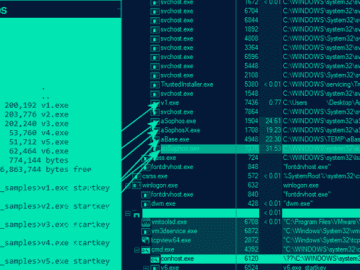
Apr 24, 2023Ravie LakshmananEndpoint Security / BYOVD Threat actors are employing a previously undocumented “defense evasion tool” dubbed AuKill that’s…
Reducing risk is fundamental to Wix’s approach to cybersecurity, and as the threat landscape evolves, they turn to HackerOne Bounty…
APC’s Easy UPS Online Monitoring Software is vulnerable to unauthenticated arbitrary remote code execution, allowing hackers to take over devices…