How Are Bug Bounty Programs and Vulnerability Disclosure Programs Different? Let’s start with the similarities. Both bug bounties and VDPs…
Japanese Cybersecurity experts have found that ChatGPT could write code for malware by entering a prompt that makes the AI…
In recent years, the term “offensive cyber capabilities” has become increasingly common in discussions around national security and military strategies….
Our Crowdsource ethical hacker community has been busy sending us security updates, including 0-day research. For Asset Monitoring, we now push out tests more…
More than ever, organizations are relying on third parties to streamline operations, scale their business, expand and leverage expertise, and…
Apple’s competitors haven’t solved the trinity of quality, design, and ecosystem Created/Updated: October 31, 2022 People are blown away that…
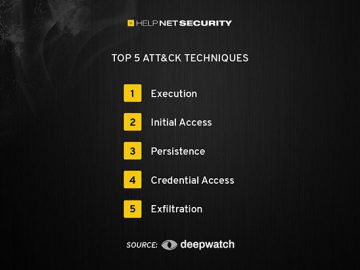
Ransomware operators have been increasingly launching frequent attacks, demanding higher ransoms, and publicly exposing victims, leading to the emergence of…
This improved experience reduces time to launch, which is vital when your organization is up against an urgent timeline to…
Patented.ai has released its introductory tool, LLM Shield that allows companies to safeguard their most sensitive data – proprietary source…
At Detectify, we’re on a journey to make the Internet more secure with the powerful combination of security automation and…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | October 31, 2022…
As shown in Figure 1 below, even early reviews can provide value. Figure 1: An early PullRequest code review. Catching…