[ This article was originally published here ] This is the third blog in the series focused on PCI DSS,…
Apr 19, 2023Ravie LakshmananCyber Threat / Malware The cyber espionage actor tracked as Blind Eagle has been linked to a…
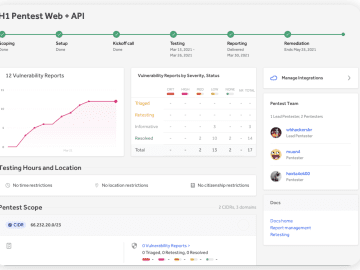
New capabilities improve pentesting to increase attack resistance The enhanced features drive robust security testing practices with the ability to…
Print management software developer PaperCut is warning customers to update their software immediately, as hackers are actively exploiting flaws to…
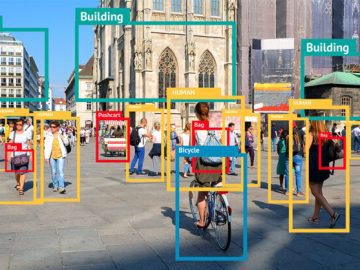
Meta, the parent company of Facebook, has introduced a new AI model to the world that can identify objects in…
Apr 19, 2023Ravie LakshmananCyber War / Cyber Attack Elite hackers associated with Russia’s military intelligence service have been linked to…
Detectify is aiming to make security understandable and easy to work with. That is why we visualize your security status…
The UK government is failing to protect workers from being “exploited” by artificial intelligence (AI) technologies, which if left unchecked…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | January 23, 2023…
A practical guide to moving to cloud services with minimal downtime, using AWS examples. For an application that’s ready to…
Online casinos and other gambling websites have revolutionized how many gamblers play. Whereas gambling used to be restricted to specific…
Apr 19, 2023Ravie LakshmananBrowser Security / Zero-Day Google on Tuesday rolled out emergency fixes to address another actively exploited high-severity…