Jun 01, 2023Ravie LakshmananCyber Threat / Network Security An analysis of the “evasive and tenacious” malware known as QBot has…
Research Highlights HackerOne has been working with economics and policy researchers from MIT and Harvard to study the economic forces…
Google announced today that bug bounty hunters who report sandbox escape chain exploits targeting its Chrome web browser are now…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
Jun 01, 2023Ravie LakshmananCybercrime / Malware Cybersecurity researchers have unmasked the identity of one of the individuals who is believed…
Russian cybersecurity firm Kaspersky says some iPhones on its network were hacked using an iOS vulnerability that installed malware via…
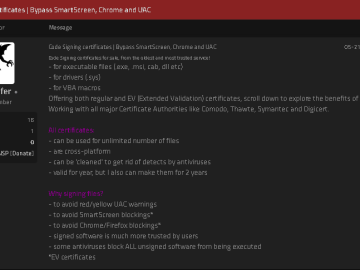
Code-signing certificates are supposed to help authenticate the identity of software publishers, and provide cryptographic assurance that a signed piece…
The shifting landscape of cybersecurity poses significant challenges for traditional vulnerability management approaches. The difficulties often arise from a lack…
Jun 01, 2023Ravie LakshmananMobile Security / APT A previously unknown advanced persistent threat (APT) is targeting iOS devices as part…
A world wide war is being waged in which the most able-bodied soldiers are being discouraged from enlisting. It is…
The FTC’s investigation found that the recordings, also including sensitive geolocation data, were used to train the Alexa voice assistant…
A recent ransomware attack on a New York-based biotech company, Enzo Biochem, has resulted in the exposure of sensitive information…