Step 1 – Recovering the corrupted data According to the doc, the following stream is corrupted: 7b 0a 20 a0…
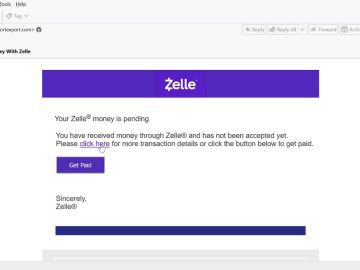
Cybercriminals have been leveraging social engineering techniques to impersonate the popular US-based digital payments network Zelle and steal money from…
Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities…
Validate security policies like you mean it Not everything on your attack surface is a vulnerability. Every organization has their…
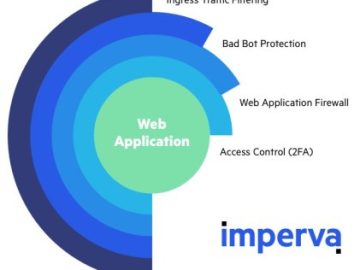
Cybercriminals are always on the lookout to exploit web application vulnerabilities. Over the years, hacking techniques and methods employed by…
What if we could send AI a message as soon as it wakes up? Created/Updated: April 3, 2023 There is…
Basic security best practices to share with your non-technical friend. Readers of my blog typically know more about technology and…
Note that during these interviews I also moderate thus quality may vary. Profile 🐝 Head of research at Portswigger University…
Cyber attacks on public websites have become an increasing concern for governments across the world, and this article is related…
As artificial intelligence (AI) technologies become more prevalent in enterprise environments, chatbots like ChatGPT are gaining popularity due to their…
The Hidden Gems Of The Burp Suite Settings [April 2023 version] Source link
A critical security issue has been discovered by the Japanese Vulnerability Notes (JVN) with the Kyocera Android printing app. The…







![The Hidden Gems Of The Burp Suite Settings [April 2023 version] The Hidden Gems Of The Burp Suite Settings [April 2023 version]](https://image.cybernoz.com/wp-content/uploads/2023/04/The-Hidden-Gems-Of-The-Burp-Suite-Settings-April-2023-360x270.jpg)
