Endpoint management and security is not one of the top areas of discussion regarding IT security, and this doesn’t come…
The new Python-based Legion malware is being linked to a potential Indonesian developer. Cloud forensics and incident response platform startup,…
More than 360,000 unique hosts appear to be at risk from three newly disclosed vulnerabilities – one of them rated…
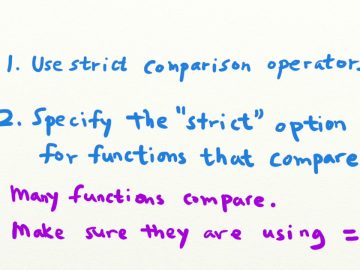
How to prevent PHP type juggling vulnerabilities Source link
WhatsApp announced today the introduction of several new security features, one of them dubbed “Device Verification” and designed to provide…
The UK’s National Cyber Security Centre (NCSC) has joined with its counterparts in Australia, Canada, Germany, the Netherlands, New Zealand…
Yorkshire Post Building Demolition #3 Source link
Poland’s Military Counterintelligence Service and its Computer Emergency Response Team have linked APT29 state-sponsored hackers, part of the Russian government’s…
Today, Outpost24 announced the release of a new Vulnerability Risk Management solution, Outscan NX. The utilisation of threat intelligence-led vulnerability…
AstraZeneca has opened an African innovation hub that will use the latest technologies to improve the healthcare of the continent’s…
Hey there, I hope you’ve been doing well! Easter Ah Easter, the American holiday where we celebrate the resurrection of…
Research estimates that the average smartphone user has 80 apps on their device, and many companies leverage their own app…









![[tl;dr sec] #177 – AWS KMS Threat Model, DOM Invader, Forensics in the Cloud [tl;dr sec] #177 - AWS KMS Threat Model, DOM Invader, Forensics in the Cloud](https://image.cybernoz.com/wp-content/uploads/2023/04/tldr-sec-177-AWS-KMS-Threat-Model-DOM-Invader-360x270.jpg)
