A critical vulnerability CVE-2025-42922 has been discovered in SAP NetWeaver that allows an authenticated, low-privileged attacker to execute arbitrary code…
Microsoft has released a warning about two serious security flaws in Windows BitLocker that could allow attackers to gain elevated…
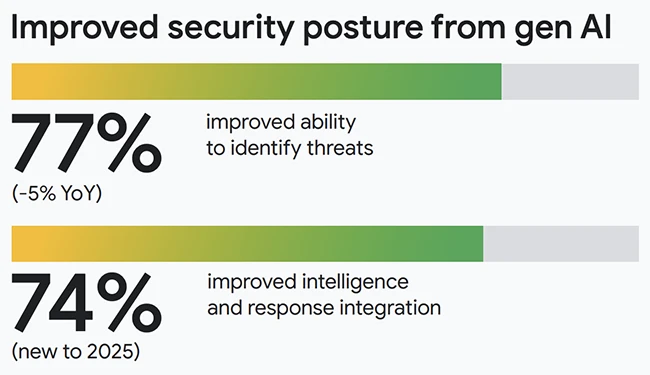
AI agents are being deployed inside enterprises today to handle tasks across security operations. This shift creates new opportunities for…
Harnessing existing capabilities For many organisations, the starting point for defining a cyber resilience strategy was the organisation’s existing business…
Microsoft has addressed two significant elevation of privilege vulnerabilities affecting its Windows BitLocker encryption feature. The flaws, tracked as CVE-2025-54911…
A critical security vulnerability has been discovered in SAP NetWeaver AS Java Deploy Service that enables authenticated attackers to execute arbitrary code…
Deception and media manipulation have always been part of warfare, but AI has taken them to a new level. Entrust…
GitHub repositories for malware delivery through sophisticated weaponized LNK files, according to recent analysis by S2W’s Threat Intelligence Center, TALON….
LLMs can make mistakes, leak data, or be tricked into doing things they were not meant to do. Garak is…
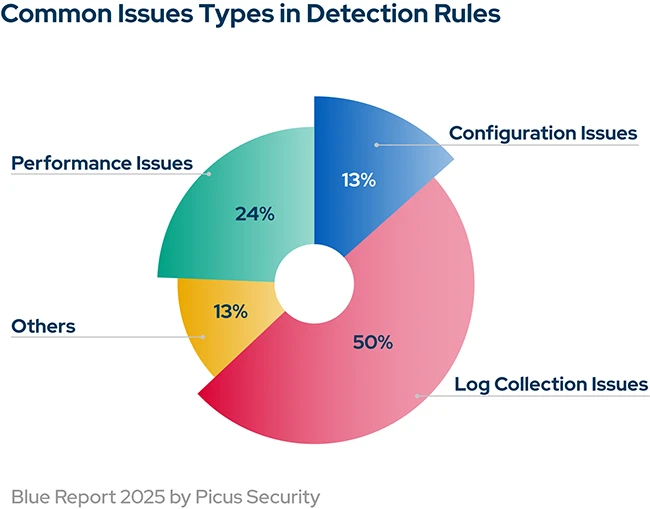
Organizations often operate as if their security controls are fully effective simply because they’re deployed, configured, and monitored. Firewalls are…
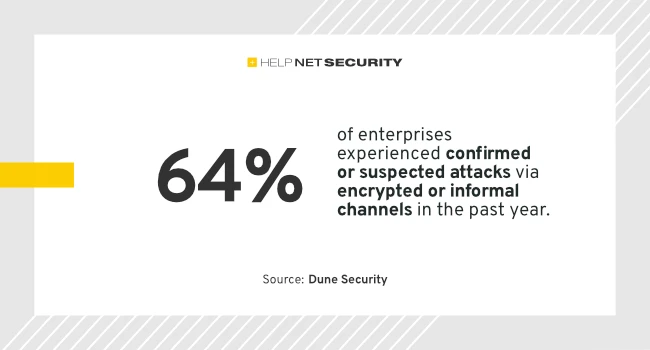
Breaches continue to grow in scale and speed, yet the weakest point remains unchanged: people. According to Dune Security’s 2025…
Workday has confirmed it suffered a data breach after a security incident involving a third-party application that compromised customer information….