Mar 22, 2023Ravie LakshmananDevOpsSec / Malware The NuGet repository is the target of a new “sophisticated and highly-malicious attack” aiming…
WellinTech KingHistorian, a software system that helps analyze data from industrial control systems, is vulnerable to a serious security flaw….
How does Bug Bounty work anyway? Source link
So far, the geologists across the globe had a brief opportunity to detect life on Mars. But a new study…
Google has announced the startups chosen for its Cybersecurity Startups Growth Academy. The 15 selected startups are from eight countries…
General Bytes acknowledged and admitted a security incident that impacted its systems between March 17 and 18. The bitcoin ATM…
How They Got Hacked Episode Fifty Six 56 Source link
Not only do security vulnerabilities lurk within software, but they can also be embedded directly into hardware, leaving technical applications…
Mar 22, 2023Ravie LakshmananNetwork Security / Cyber Threat The threat group tracked as REF2924 has been observed deploying previously unseen…
WellinTech KingHistorian, a time-series database used for industrial control system data analysis, is vulnerable to an integer conversion vulnerability. This…
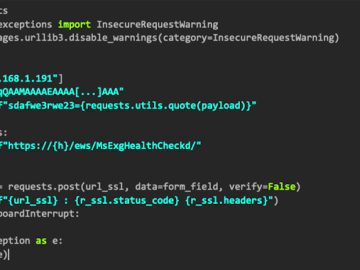
In this write-up, I want to share a cool way in which I was able to bypass firewall limitations that…
“Is cybersecurity recession-proof?” That’s the question on the minds of many security professionals and executives as a possible economic downturn…