It’s -30 Celsius in December. An entire city has gone dark. There is no electricity, heating, internet, or telecommunications—all because…
The cybersecurity researchers at Google identified eighteen zero-day vulnerabilities, four of which allowed Hackers to remotely compromise smartphone devices using…
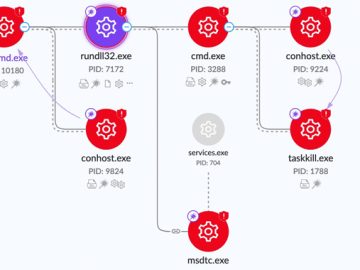
Mar 20, 2023Ravie LakshmananEndpoint Security / Ransomware The threat actors behind the CatB ransomware operation have been observed using a…
US cyber attacks 2023 report is here and the result is alarming. The United States of America has a nominal…
curl disclosed a bug submitted by kurohiro: https://hackerone.com/reports/1897203 Source link
Tracking pixels like the Meta and TikTok pixels are popular tools for online businesses to monitor their website visitors’ behaviors…
Mar 20, 2023The Hacker NewsData Breach / Dark Web This article has not been generated by ChatGPT. 2022 was the…
Practical Junior Malware Researcher (PJMR) Exam Overview Source link
If you can believe it, it’s been a decade since the annual European Cybersecurity Blogger Awards initially launched in 2013!…
Waterfall Security Solutions launched the WF-600 Unidirectional Security Gateway, an OT security protection against remote cyber attacks. The WF-600 product…
Anonymous Sudan has targeted several nations and has named their healthcare providers, universities, government websites, and even airports to its…
Mullvad’s FREE DNS over HTTPS service is a no-brainer for these reasons Source link